WordPress firewalls are web application firewalls (WAFs) created primarily to safeguard WordPress websites.
WAFs are relatively new to the industry of web security. This guide explains what firewalls are and how they became WAFs. It also describes the various types of WordPress firewalls on the market and how they operate.
The Idea Behind Firewalls
A firewall is established between two or more networks to manage the incoming and outgoing traffic of each network. It serves as a barrier between a trusted network and an unsecured network.
A firewall is typically implemented between an Internet connection and an internal network in a conventional configuration. It is utilized to defend the network against incoming Internet threats. Moreover, it is used to regulate who can access the internet. If you use a WiFi router at home, the router also serves as your home's firewall. Almost all residential Wi-Fi routers include a firewall today.
1st-Generation Firewalls — Packet Filtering Evolving Into Web Application Firewalls
Initially, firewalls were intended to restrict and control network traffic. They just performed packet filtering and did not comprehend the payload of the transmission. If you hosted a website on your network, you had to expose port 80 to the public through the firewall.
Once a port is opened, the firewall allows any type of incoming traffic, including malicious traffic, to pass through it.
2nd Generation – Stateful Filtering
The firewalls of the second generation worked on Layer 4 of the OSI model. This indicates that they are able to determine the sort of connection they are managing. For instance, if a packet is establishing a new connection or if the connection has already been established, etc.
Despite this, firewalls of the second generation have many problems in regulating traffic. Administrators could at least define firewall rules based on connection status.
Application Layer Filtering in 3rd Generation Firewalls
Today's firewalls were introduced in the mid-1990s. Modern firewall technology is aware of protocols and apps. Hence, firewalls of the third generation can determine if a packet's payload is for an FTP server and what the request is, or whether it is an HTTP connection request and what the request is.
This technology led to the creation of firewalls with a limited scope, such as Web Application Firewalls.
WordPress Firewalls / Web Application Firewalls
WordPress Firewall schematic
Web application firewalls have a limited scope. On a network, their duty is to defend a website from dangerous hacker attacks.
A WordPress firewall is a web application firewall created specifically to safeguard WordPress. When a WordPress firewall is implemented on a WordPress site, it analyzes all incoming HTTP requests from the internet.
When an HTTP request's payload is malicious, the WordPress firewall terminates the connection.
How are WordPress firewalls implemented?
A WordPress firewall identifies harmful requests in a manner similar to that of anti-malware software. Signatures are a collection of known attacks, and when the payload of an HTTP request matches a signature, the request is malicious.
The majority of WordPress firewalls do not permit the modification of attack signatures. But, web application firewalls that are not WordPress-centric are highly adjustable. You can customize them precisely for your website, whether you're using WordPress or a custom solution. You can design your own security policies, exceptions, etc. When configuring a web application firewall, care must be taken not to prevent legitimate traffic.
Moreover, some web application firewalls feature auto-learn technologies. This heuristic technology examines your website's traffic to determine which visitors are legitimate and which are not.
Various WordPress Firewall Types
Firewall WordPress Plugins
The majority of WordPress firewalls that are self-hosted are WordPress plugins. When a plugin firewall is installed, each HTTP request received to your website is handled as follows:
- First, it is received by the web server service (Apache or Nginx).
- Next it initiates the WordPress bootstrap/load procedure, which initializes WordPress (wp-config.php, initializes the database connection, WordPress settings etc).
- Before WordPress actually processes the request, the WordPress firewall plugin parses it.
WordPress firewall plugins are perfect for SMBs due to their low cost and user-friendliness. Also, the majority of them have malware scanners integrated. Yet, these firewalls are active on your site and were initiated by WordPress. Hence, if there is a vulnerability on your site prior to the firewall being activated, there is a potential that attackers can get complete access to your WordPress site.
Firewalls Appliance for WordPress Web Application
Firewalls for web applications in general can also be utilized as WordPress firewalls. This could be a dedicated piece of hardware or software.
Installing generic web application firewalls between your WordPress website and the Internet connection. So, each HTTP request sent to your WordPress site must first via the WAF. These WAFs are unquestionably more secure than WordPress firewall plugins. Unfortunately, they are costly and require specialized technical knowledge to manage. Therefore, they are rarely utilized by small enterprises.
WordPress Website Cloud Firewalls (SaaS)
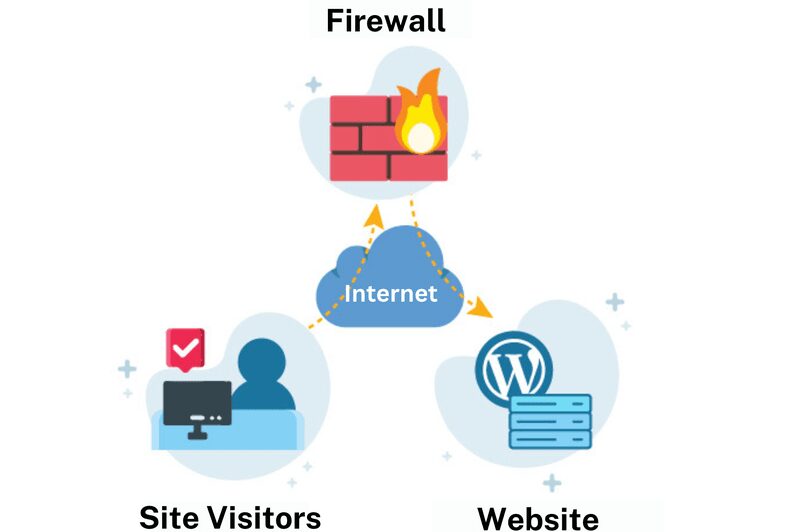
WordPress Cloud Firewall, unlike self-hosted firewall plugins or appliances, does not need to be deployed on the same network as your web server. It is an internet service that functions as a proxy server, filtering your website's traffic before forwarding it to your domain.
By using an online WordPress firewall, your domain's DNS records are configured to point to the online WAF. This implies that your website visitors speak with the online WordPress firewall and not with your WordPress site directly.
A typical online firewall has multiple scopes. In addition to securing your WordPress site from hack assaults, it can also operate as a caching server and content delivery network (CDN). Comparing online web application firewalls to self-hosted generic web application firewalls reveals that online web application firewalls are also very cost-effective.
Cloud Firewall/WAF can be Bypassed.
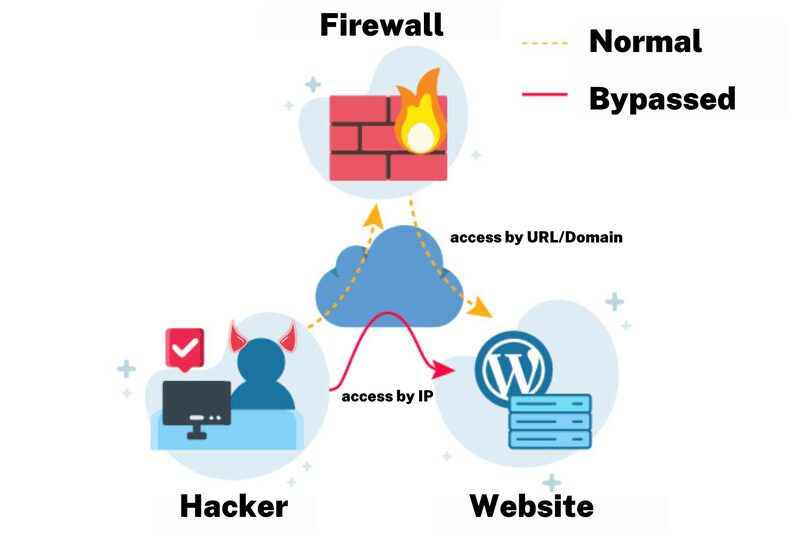
For the WAF to forward traffic to your WordPress site, there is a constraint of online WordPress firewalls that your web server must be available over the internet. This implies that anyone who knows the IP address of your web server can still communicate directly with it.
So, in non-targeted WordPress attacks, in which attackers scan whole networks for susceptible sites, your web server and website remain directly accessible. To avoid falling victim to such an attack, you can configure your server's firewall to only reply to traffic originating from the online WordPress firewall.
Limiting Generic Restrictions of WordPress Firewalls Zero-Day Vulnerability Defense
Checking an HTTP request's payload against a database of signatures is one of the most prevalent WAF protection techniques. Hence, when a user accesses your website, the WAF compares the payload against a database of known web assaults. If it matches, it is harmful; if not, it is allowed through.
In the event of a zero-day WordPress vulnerability, there is a possibility that your WordPress firewall will not prevent the assault. Because of this, vendor responsiveness is vital, and you should only utilize software from responsive and reputable companies. It is preferable if the vendor can change the firewall rules as soon as possible.
Bypassing Web Application Firewall
Web application firewalls are software like any other. They have their own problems and can have weaknesses. In fact, there are a significant number of white papers and articles discussing strategies used to circumvent web application firewall protection. Nonetheless, as long as the vendor is attentive and remediates such problems in a timely manner, all is OK.
Should You Use a Firewall with WordPress?
Definitely! Which firewall should you use with WordPress? Each WordPress firewall has advantages and disadvantages, so choose the one that best meets your needs. Therefore, even if you have a WordPress firewall, you must be vigilant.
Regarding WordPress security, there is no failsafe solution. Hence, you must always harden > monitor > enhance > test. Maintain a WordPress site activity record, create a rock-solid WordPress backup solution, and employ a WordPress firewall. These organizations are ones we endorse and like working with:

